The second Patch Tuesday of 2021 is relatively light on the vulnerability count, with 64 CVEs being addressed across the majority of Microsoft’s product families. Despite that, there’s still plenty to discuss this month.
Vulnerability Breakdown by Software Family
| Family | Vulnerability Count |
|---|
| Windows | 28 |
| ESU | 14 |
| Microsoft Office | 11 |
| Browser | 9 |
| Developer Tools | 8 |
| Microsoft Dynamics | 2 |
| Exchange Server | 2 |
| Azure | 2 |
| System Center | 2 |
Exploited and Publicly Disclosed Vulnerabilities
One zero-day was announced: CVE-2021-1732 is a privilege elevation vulnerability affecting the Win32k component of Windows 10 and Windows Server 2019, reported to be exploited in the wild. Four vulnerabilities have been previously disclosed: CVE-2021-1727, a privilege elevation vulnerability in Windows Installer, affecting all supported versions of Windows; CVE-2021-24098, which is a denial of service (DoS) affecting Windows 10 and Server 2019; CVE-2021-24106, an information disclosure vulnerability affecting DirectX in Windows 10 and Server 2019; and CVE-2021-26701, an RCE in .NET Core.
Vulnerabilities in Windows TCP/IP
Microsoft also disclosed a set of three serious vulnerabilities affecting the TCP/IP networking stack in all supported versions of Windows. Two of these (CVE-2021-24074 and CVE-2021-24094) carry a base CVSSv3 score of 9.8 and could allow Remote Code Execution (RCE). CVE-2021-24094 is specific to IPv6 link-local addresses, meaning it isn’t exploitable over the public internet. CVE-2021-24074, however, does not have this limitation. The third, CVE-2021-24086, is a DoS vulnerability that could allow an attacker to trigger a “blue screen of death” on any Windows system that is directly exposed to the internet, using only a small amount of network traffic. The RCE exploits are probably not a threat in the short term, due to the complexity of the vulnerabilities, but DoS attacks are expected to be seen much more quickly. Windows systems should be patched as soon as possible to protect against these.
In the event a patch cannot be applied immediately, such as on systems that cannot be rebooted, Microsoft has published mitigation guidance that will protect against exploitation of the TCP/IP vulnerabilities. Depending on the exposure of an asset, IPv4 Source Routing should be disabled via a Group Policy or a Netsh command, and IPv6 packet reassembly should be disabled via a separate Netsh command. IPv4 Source Routing requests and IPv6 fragments can also be blocked load balancers, firewalls, or other edge devices to mitigate these issues.
Zerologon Update
Back in August, 2020, Microsoft addressed a critical remote code vulnerability (CVE-2020-1472) affecting the Netlogon protocol (MS-NRPC), a.k.a. “Zerologon”. In October, Microsoft noted that attacks which exploit this weakness have been seen in the wild. On January 14, 2021, they reminded organizations that the February 2021 security update bundle will also be enabling “Domain Controller enforcement mode" by default to fully address this weakness. Any system that tries to make an insecure Netlogon connection will be denied access. Any business-critical process that relies on these insecure connections will cease to function. Rapid7 encourages all organizations to heed the detailed guidance before applying the latest updates to ensure continued business process continuity.
Adobe
Most important amongst the six security advisories published by Adobe today is APSB21-09, detailing 23 CVEs affecting Adobe Acrobat and Reader. Six of these are rated Critical and allow Arbitrary Code Execution, and one of which (CVE-2021-21017), has been seen exploited in the wild in attacks targeting Adobe Reader users on Windows.
Summary Tables
Azure Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-24109 | Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability | No | No | 6.8 | Yes |
| CVE-2021-24087 | Azure IoT CLI extension Elevation of Privilege Vulnerability | No | No | 7 | Yes |
Browser Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-24100 | Microsoft Edge for Android Information Disclosure Vulnerability | No | No | 5 | Yes |
| CVE-2021-24113 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | No | No | 4.6 | Yes |
| CVE-2021-21148 | Chromium CVE-2021-21148: Heap buffer overflow in V8 | N/A | N/A | nan | Yes |
| CVE-2021-21147 | Chromium CVE-2021-21147: Inappropriate implementation in Skia | N/A | N/A | nan | Yes |
| CVE-2021-21146 | Chromium CVE-2021-21146: Use after free in Navigation | N/A | N/A | nan | Yes |
| CVE-2021-21145 | Chromium CVE-2021-21145: Use after free in Fonts | N/A | N/A | nan | Yes |
| CVE-2021-21144 | Chromium CVE-2021-21144: Heap buffer overflow in Tab Groups | N/A | N/A | nan | Yes |
| CVE-2021-21143 | Chromium CVE-2021-21143: Heap buffer overflow in Extensions | N/A | N/A | nan | Yes |
| CVE-2021-21142 | Chromium CVE-2021-21142: Use after free in Payments | N/A | N/A | nan | Yes |
Developer Tools Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-26700 | Visual Studio Code npm-script Extension Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-1639 | Visual Studio Code Remote Code Execution Vulnerability | No | No | 7 | No |
| CVE-2021-1733 | Sysinternals PsExec Elevation of Privilege Vulnerability | No | Yes | 7.8 | Yes |
| CVE-2021-24105 | Package Managers Configurations Remote Code Execution Vulnerability | No | No | 8.4 | Yes |
| CVE-2021-24111 | .NET Framework Denial of Service Vulnerability | No | No | 7.5 | No |
| CVE-2021-1721 | .NET Core and Visual Studio Denial of Service Vulnerability | No | Yes | 6.5 | No |
| CVE-2021-26701 | .NET Core Remote Code Execution Vulnerability | No | Yes | 8.1 | Yes |
| CVE-2021-24112 | .NET Core Remote Code Execution Vulnerability | No | No | 8.1 | Yes |
ESU Windows Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-24080 | Windows Trust Verification API Denial of Service Vulnerability | No | No | 6.5 | No |
| CVE-2021-24074 | Windows TCP/IP Remote Code Execution Vulnerability | No | No | 9.8 | Yes |
| CVE-2021-24094 | Windows TCP/IP Remote Code Execution Vulnerability | No | No | 9.8 | Yes |
| CVE-2021-24086 | Windows TCP/IP Denial of Service Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-1734 | Windows Remote Procedure Call Information Disclosure Vulnerability | No | No | 7.5 | Yes |
| CVE-2021-25195 | Windows PKU2U Elevation of Privilege Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-24088 | Windows Local Spooler Remote Code Execution Vulnerability | No | No | 8.8 | No |
| CVE-2021-1727 | Windows Installer Elevation of Privilege Vulnerability | No | Yes | 7.8 | No |
| CVE-2021-24077 | Windows Fax Service Remote Code Execution Vulnerability | No | No | 9.8 | Yes |
| CVE-2021-1722 | Windows Fax Service Remote Code Execution Vulnerability | No | No | 8.1 | Yes |
| CVE-2021-24102 | Windows Event Tracing Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-24103 | Windows Event Tracing Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-24078 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 9.8 | Yes |
| CVE-2021-24083 | Windows Address Book Remote Code Execution Vulnerability | No | No | 7.8 | No |
Exchange Server Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-24085 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 6.5 | Yes |
| CVE-2021-1730 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 5.4 | Yes |
Microsoft Dynamics Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-1724 | Microsoft Dynamics Business Central Cross-site Scripting Vulnerability | No | No | 6.1 | No |
| CVE-2021-24101 | Microsoft Dataverse Information Disclosure Vulnerability | No | No | 6.5 | Yes |
Microsoft Office Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-24073 | Skype for Business and Lync Spoofing Vulnerability | No | No | 6.5 | No |
| CVE-2021-24099 | Skype for Business and Lync Denial of Service Vulnerability | No | No | 6.5 | No |
| CVE-2021-24114 | Microsoft Teams iOS Information Disclosure Vulnerability | No | No | 5.7 | Yes |
| CVE-2021-1726 | Microsoft SharePoint Spoofing Vulnerability | No | No | 8 | Yes |
| CVE-2021-24072 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 | No |
| CVE-2021-24066 | Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2021-24071 | Microsoft SharePoint Information Disclosure Vulnerability | No | No | 5.3 | Yes |
| CVE-2021-24067 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-24068 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-24069 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
| CVE-2021-24070 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 | Yes |
System Center Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-1728 | System Center Operations Manager Elevation of Privilege Vulnerability | No | No | 8.8 | Yes |
| CVE-2021-24092 | Microsoft Defender Elevation of Privilege Vulnerability | No | No | 7.8 | Yes |
Windows Vulnerabilities
| CVE | Vulnerability Title | Exploited | Publicly Disclosed | CVSSv3 Base Score | FAQ? |
|---|
| CVE-2021-1732 | Windows Win32k Elevation of Privilege Vulnerability | Yes | No | 7.8 | No |
| CVE-2021-1698 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-24075 | Windows Network File System Denial of Service Vulnerability | No | No | 6.8 | No |
| CVE-2021-24084 | Windows Mobile Device Management Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2021-24096 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 | No |
| CVE-2021-24093 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 8.8 | Yes |
| CVE-2021-24106 | Windows DirectX Information Disclosure Vulnerability | No | Yes | 5.5 | Yes |
| CVE-2021-24098 | Windows Console Driver Denial of Service Vulnerability | No | Yes | 5.5 | Yes |
| CVE-2021-24091 | Windows Camera Codec Pack Remote Code Execution Vulnerability | No | No | 7.8 | No |
| CVE-2021-24079 | Windows Backup Engine Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2021-1731 | PFX Encryption Security Feature Bypass Vulnerability | No | No | 5.5 | Yes |
| CVE-2021-24082 | Microsoft.PowerShell.Utility Module WDAC Security Feature Bypass Vulnerability | No | No | 4.3 | No |
| CVE-2021-24076 | Microsoft Windows VMSwitch Information Disclosure Vulnerability | No | No | 5.5 | Yes |
| CVE-2021-24081 | Microsoft Windows Codecs Library Remote Code Execution Vulnerability | No | No | 7.8 | No |
Summary Charts
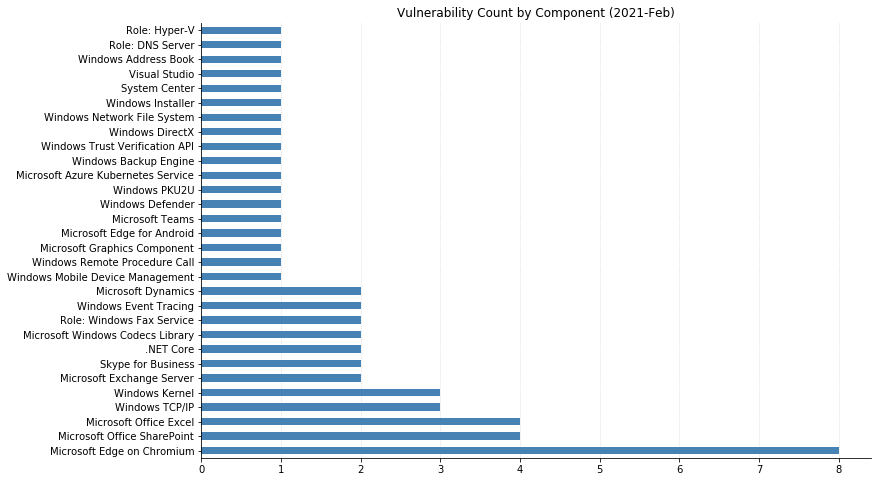
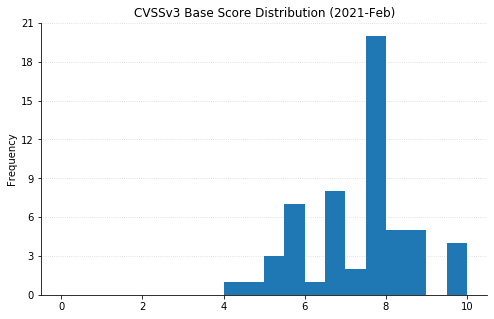
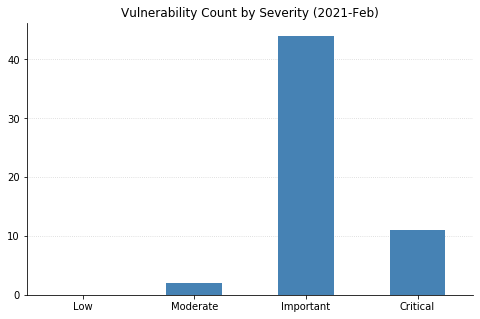
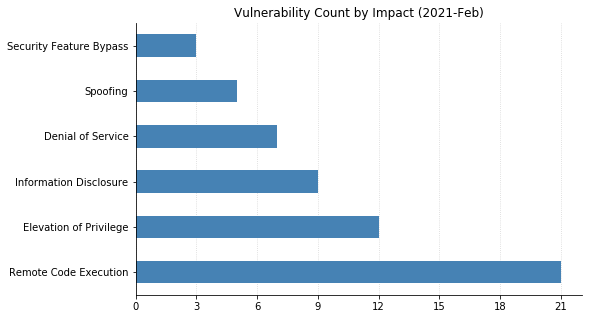
Note: Chart data is reflective of data presented by Microsoft's CVRF at the time of writing.




