It’s a relatively light Patch Tuesday this month by the numbers – Microsoft has only published 67 new CVEs, most of which affect their flagship Windows operating system. However, four of these are zero-days, having been observed as exploited in the wild.
The big news is that two older zero-day CVEs affecting Exchange Server, made public at the end of September, have finally been fixed. CVE-2022-41040 is a “Critical” elevation of privilege vulnerability, and CVE-2022-41082 is considered Important, allowing Remote Code Execution (RCE) when PowerShell is accessible to the attacker. Both vulnerabilities have been exploited in the wild. Four other CVEs affecting Exchange Server have also been addressed this month. Three are rated as Important, and CVE-2022-41080 is another privilege escalation vulnerability considered Critical. Customers are advised to update their Exchange Server systems immediately, regardless of whether any previously recommended mitigation steps have been applied. The mitigation rules are no longer recommended once systems have been patched.
Three of the new zero-day vulnerabilities are:
- CVE-2022-41128, a Critical RCE affecting the JScript9 scripting language (Microsoft’s legacy JavaScript dialect, used by their Internet Explorer browser).
- CVE-2022-41073 is the latest in a storied history of vulnerabilities affecting the Windows Print Spooler, allowing privilege escalation and considered Important.
- CVE-2022-41125 is also an Important privilege escalation vulnerability, affecting the Windows Next-generation Cryptography (CNG) Key Isolation service.
The fourth zero-day, CVE-2022-41091, was previously disclosed and widely reported on in October. It is a Security Feature Bypass of “Windows Mark of the Web” – a mechanism meant to flag files that have come from an untrusted source.
Exchange Server admins are not the only ones on the hook this month: SharePoint Server is affected by CVE-2022-41062, an Important RCE that could allow an attacker who has Site Member privileges to execute code remotely on the server. CVE-2022-41122, a Spoofing vulnerability that Microsoft rates as “Exploitation more likely” than not, was actually addressed in September’s SharePoint patches but not included in their Security Update Guide at the time.
This month also sees Microsoft’s third non-CVE security advisory of the year, ADV220003, which is a “defense-in-depth” update for older versions of Microsoft Office (2013 and 2016) that improves validation of documents protected via Microsoft’s Information Rights Management (IRM) technology – a feature of somewhat dubious value, meant to help prevent sensitive information from being printed, forwarded, or copied without authorization.
Summary charts
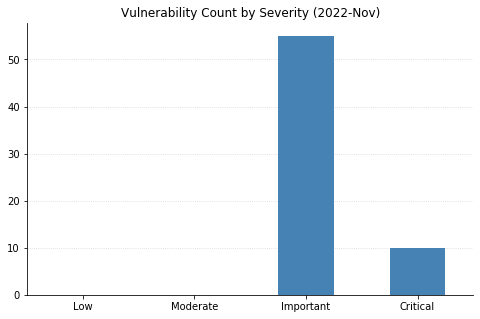
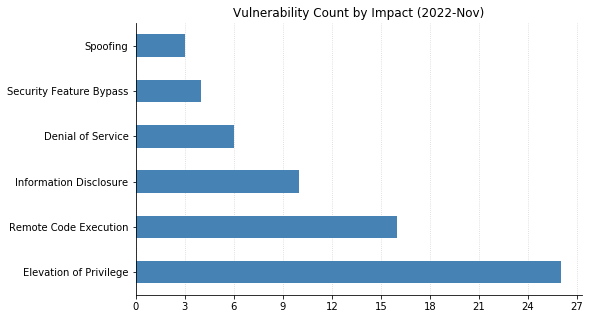
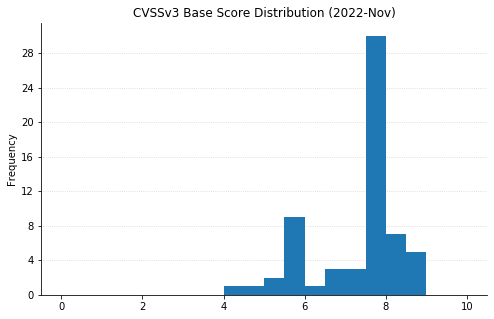
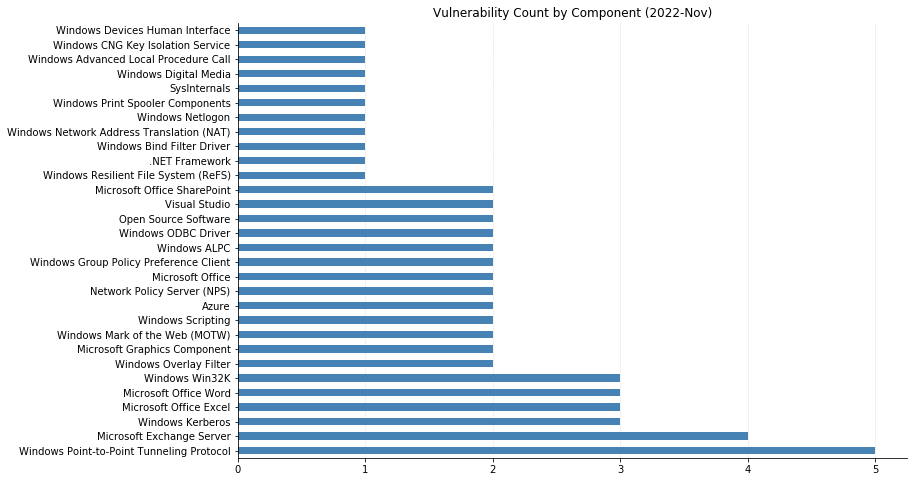
Summary tables
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41051 | Azure RTOS GUIX Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41085 | Azure CycleCloud Elevation of Privilege Vulnerability | No | No | 7.5 |
| CVE-2022-39327 | GitHub: CVE-2022-39327 Improper Control of Generation of Code ('Code Injection') in Azure CLI | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41119 | Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41120 | Microsoft Windows Sysmon Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41064 | .NET Framework Information Disclosure Vulnerability | No | No | 5.8 |
| CVE-2022-39253 | GitHub: CVE-2022-39253 Local clone optimization dereferences symbolic links by default | No | No | N/A |
ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41044 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2022-41116 | Windows Point-to-Point Tunneling Protocol Denial of Service Vulnerability | No | No | 5.9 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41128 | Windows Scripting Languages Remote Code Execution Vulnerability | Yes | No | 8.8 |
| CVE-2022-41047 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2022-41048 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2022-41039 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2022-38023 | Netlogon RPC Elevation of Privilege Vulnerability | No | No | 8.1 |
| CVE-2022-41109 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41073 | Windows Print Spooler Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2022-41057 | Windows HTTP.sys Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-37992 | Windows Group Policy Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41095 | Windows Digital Media Receiver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41045 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41118 | Windows Scripting Languages Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2022-41058 | Windows Network Address Translation (NAT) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2022-41053 | Windows Kerberos Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2022-41056 | Network Policy Server (NPS) RADIUS Protocol Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability | No | No | 7.2 |
| CVE-2022-41097 | Network Policy Server (NPS) RADIUS Protocol Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2022-41086 | Windows Group Policy Elevation of Privilege Vulnerability | No | No | 6.4 |
| CVE-2022-41090 | Windows Point-to-Point Tunneling Protocol Denial of Service Vulnerability | No | No | 5.9 |
| CVE-2022-41098 | Windows GDI+ Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2022-23824 | AMD: CVE-2022-23824 IBPB and Return Address Predictor Interactions | No | No | N/A |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41080 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2022-41078 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2022-41079 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2022-41123 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 7.8 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41066 | Microsoft Business Central Information Disclosure Vulnerability | No | No | 4.4 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41062 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2022-41061 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41107 | Microsoft Office Graphics Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41106 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41063 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41122 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 6.5 |
| CVE-2022-41060 | Microsoft Word Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2022-41103 | Microsoft Word Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2022-41104 | Microsoft Excel Security Feature Bypass Vulnerability | No | No | 5.5 |
| CVE-2022-41105 | Microsoft Excel Information Disclosure Vulnerability | No | No | 5.5 |
Open Source Software Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-38014 | Windows Subsystem for Linux (WSL2) Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2022-3786 | OpenSSL: CVE-2022-3786 X.509 certificate verification buffer overrun | No | No | N/A |
| CVE-2022-3602 | OpenSSL: CVE-2022-3602 X.509 certificate verification buffer overrun | No | No | N/A |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|
| CVE-2022-41088 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2022-41092 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41113 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41054 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41101 | Windows Overlay Filter Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41102 | Windows Overlay Filter Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41052 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2022-41050 | Windows Extensible File Allocation Table Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41125 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability | Yes | No | 7.8 |
| CVE-2022-41100 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41093 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41096 | Microsoft DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2022-41114 | Windows Bind Filter Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2022-38015 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2022-41055 | Windows Human Interface Device Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability | Yes | Yes | 5.4 |
| CVE-2022-41049 | Windows Mark of the Web Security Feature Bypass Vulnerability | No | No | 5.4 |
| CVE-2022-41099 | BitLocker Security Feature Bypass Vulnerability | No | No | 4.6 |




