Microsoft is starting the new year with a bang! Today’s Patch Tuesday release addresses almost 100 CVEs. After a relatively mild holiday season, defenders and admins now have a wide range of exciting new vulnerabilities to consider.
Two zero-day vulnerabilities emerged today, both affecting a wide range of current Windows operating systems.
CVE-2023-21674 allows Local Privilege Escalation (LPE) to SYSTEM via a vulnerability in Windows Advanced Local Procedure Call (ALPC), which Microsoft has already seen exploited in the wild. Given its low attack complexity, the existence of functional proof-of-concept code, and the potential for sandbox escape, this may be a vulnerability to keep a close eye on. An ALPC zero-day back in 2018 swiftly found its way into a malware campaign.
CVE-2023-21549 is Windows SMB elevation for which Microsoft has not yet seen in-the-wild exploitation or a solid proof-of-concept, although Microsoft has marked it as publicly disclosed.
This Patch Tuesday also includes a batch of seven Critical Remote Code Execution (RCE) vulnerabilities. These are split between Windows Secure Socket Tunneling Protocol (SSTP) – source of another Critical RCE last month – and Windows Layer 2 Tunneling Protocol (L2TP). Happily, none of these has yet been seen exploited in the wild, and Microsoft has assessed all seven as “exploitation less likely” (though time will tell).
Today’s haul includes two Office Remote Code Execution vulnerabilities. Both CVE-2023-21734 and CVE-2023-21735 sound broadly familiar: a user needs to be tricked into running malicious files. Unfortunately, the security update for Microsoft Office 2019 for Mac and Microsoft Office LTSC for Mac 2021 are not immediately available, so admins with affected assets will need to check back later and rely on other defenses for now.
On the server side, five CVEs affecting Microsoft Exchange Server were addressed today: two Spoofing vulnerabilities, two Elevation of Privilege, and an Information Disclosure. Any admins who no longer wish to run on-prem Exchange may wish to add these to the evidence pile.
Anyone responsible for a SharePoint Server instance has three new vulnerabilities to consider. Perhaps the most noteworthy is CVE-2023-21743, a remote authentication bypass. Remediation requires additional admin action after the installation of the SharePoint Server security update; however, exploitation requires no user interaction, and Microsoft already assesses it as “Exploitation More Likely”. This regrettable combination of properties explains the Critical severity assigned by Microsoft despite the relatively low CVSS score.
Another step further away from the Ballmer era: Microsoft recently announced the potential inclusion of CBL-Mariner CVEs as part of Security Update Guide guidance starting as early as tomorrow (Jan 11). First released on the carefully-selected date of April 1, 2020, CBL-Mariner is the Microsoft-developed Linux distro which acts as the base container OS for Azure services, and also underpins elements of WSL2.
Farewell Windows 8.1, we hardly knew ye: today’s security patches include fixes for Windows 8.1 for the final time, since Extended Support for most editions of Windows 8.1 ends today.
Summary charts
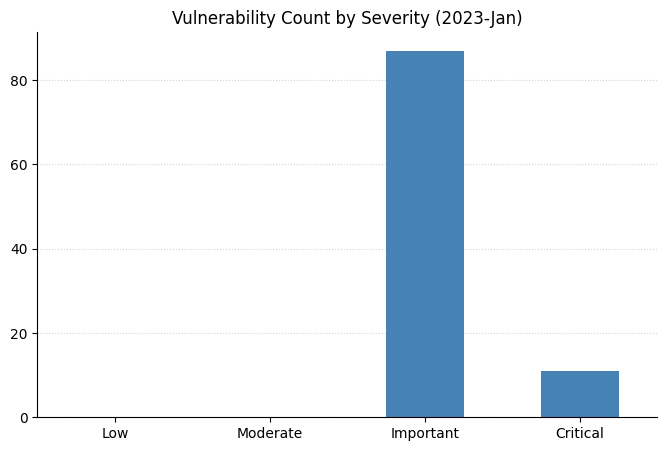
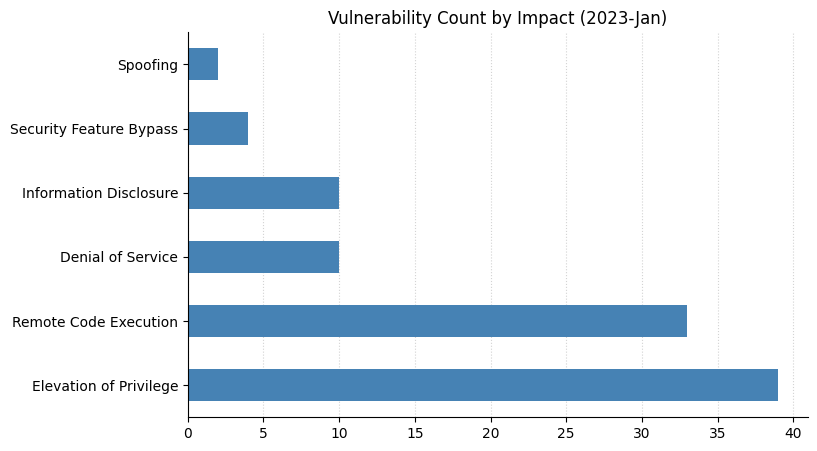
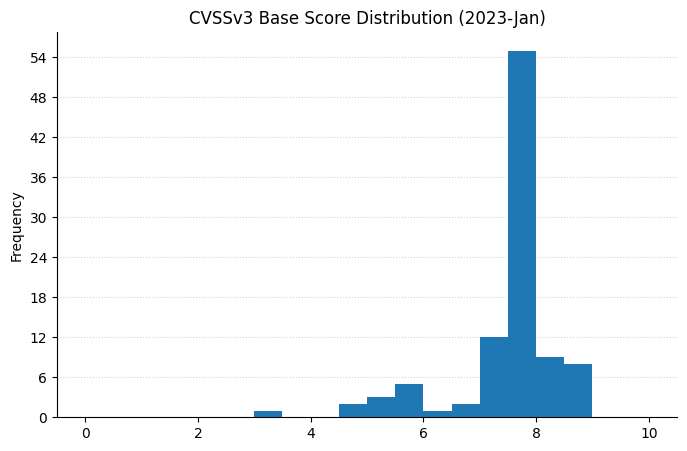
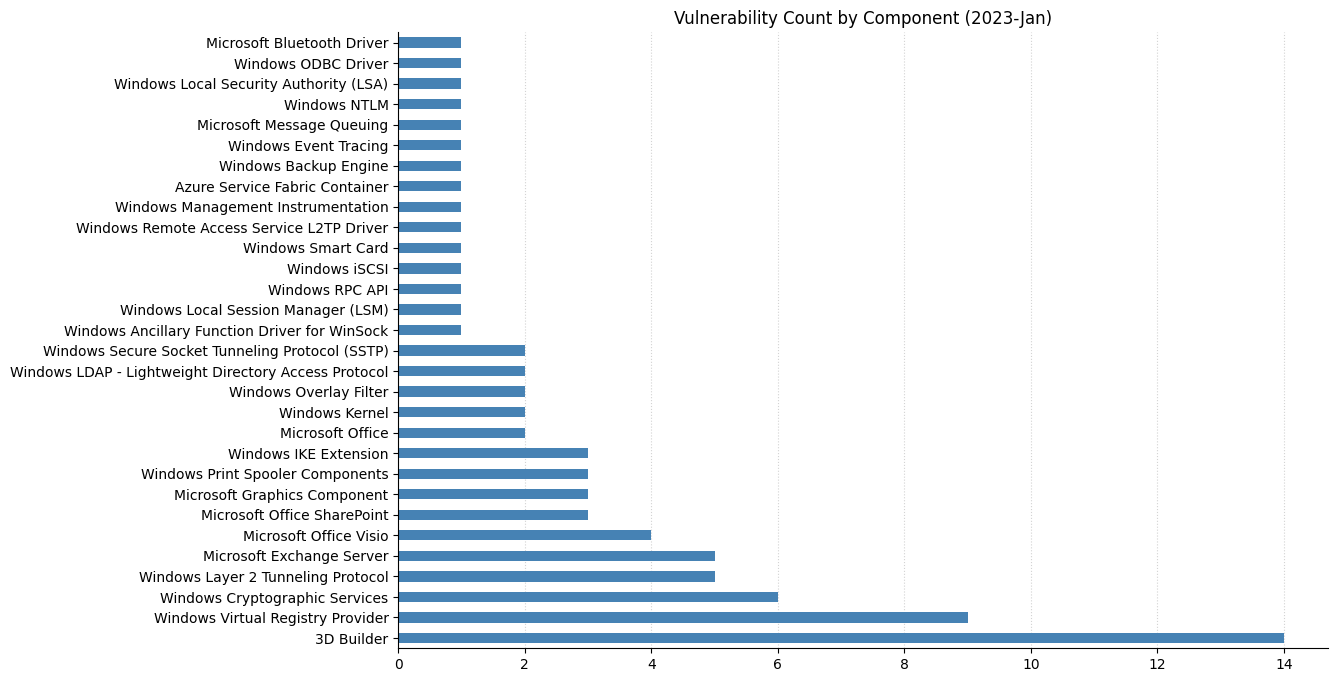
Summary tables
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21780 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21781 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21782 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21784 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21786 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21791 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21793 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21783 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21785 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21787 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21788 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21789 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21790 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21792 | 3D Builder Remote Code Execution Vulnerability | No | No | 7.8 |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21531 | Azure Service Fabric Container Elevation of Privilege Vulnerability | No | No | 7 |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21538 | .NET Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21779 | Visual Studio Code Remote Code Execution | No | No | 7.3 |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21762 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-21745 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 8 |
| CVE-2023-21763 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21764 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21761 | Microsoft Exchange Server Information Disclosure Vulnerability | No | No | 7.5 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21742 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21744 | Microsoft SharePoint Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21736 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21737 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21734 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21735 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-21738 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.1 |
| CVE-2023-21741 | Microsoft Office Visio Information Disclosure Vulnerability | No | No | 7.1 |
| CVE-2023-21743 | Microsoft SharePoint Server Security Feature Bypass Vulnerability | No | No | 5.3 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21725 | Windows Malicious Software Removal Tool Elevation of Privilege Vulnerability | No | No | 6.3 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21676 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21674 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability | Yes | No | 8.8 |
| CVE-2023-21767 | Windows Overlay Filter Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21755 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21558 | Windows Error Reporting Service Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21768 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21724 | Microsoft DWM Core Library Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21551 | Microsoft Cryptographic Services Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21677 | Windows Internet Key Exchange (IKE) Extension Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21683 | Windows Internet Key Exchange (IKE) Extension Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21758 | Windows Internet Key Exchange (IKE) Extension Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21539 | Windows Authentication Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2023-21547 | Internet Key Exchange (IKE) Protocol Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21771 | Windows Local Session Manager (LSM) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-21739 | Windows Bluetooth Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-21733 | Windows Bind Filter Driver Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-21540 | Windows Cryptographic Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-21550 | Windows Cryptographic Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-21559 | Windows Cryptographic Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-21753 | Event Tracing for Windows Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-21766 | Windows Overlay Filter Information Disclosure Vulnerability | No | No | 4.7 |
| CVE-2023-21536 | Event Tracing for Windows Information Disclosure Vulnerability | No | No | 4.7 |
| CVE-2023-21759 | Windows Smart Card Resource Management Server Security Feature Bypass Vulnerability | No | No | 3.3 |
Windows ESU vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21549 | Windows SMB Witness Service Elevation of Privilege Vulnerability | No | Yes | 8.8 |
| CVE-2023-21681 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21732 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-21561 | Microsoft Cryptographic Services Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-21535 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21548 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21546 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21543 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21555 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21556 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21679 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-21680 | Windows Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21541 | Windows Task Scheduler Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21678 | Windows Print Spooler Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21765 | Windows Print Spooler Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21746 | Windows NTLM Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21524 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21747 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21748 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21749 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21754 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21772 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21773 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21774 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21675 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21552 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21726 | Windows Credential Manager User Interface Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21537 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21730 | Microsoft Cryptographic Services Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-21527 | Windows iSCSI Service Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21728 | Windows Netlogon Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21557 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21757 | Windows Layer 2 Tunneling Protocol (L2TP) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-21760 | Windows Print Spooler Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-21750 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-21752 | Windows Backup Service Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2023-21542 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-21532 | Windows GDI Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-21563 | BitLocker Security Feature Bypass Vulnerability | No | No | 6.8 |
| CVE-2023-21560 | Windows Boot Manager Security Feature Bypass Vulnerability | No | No | 6.6 |
| CVE-2023-21776 | Windows Kernel Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-21682 | Windows Point-to-Point Protocol (PPP) Information Disclosure Vulnerability | No | No | 5.3 |
| CVE-2023-21525 | Remote Procedure Call Runtime Denial of Service Vulnerability | No | No | 5.3 |

