Microsoft is offering fixes for 101 security issues for March 2023 Patch Tuesday, including two zero-day vulnerabilities; the most interesting of the two zero-day vulnerabilities is a flaw in Outlook which allows an attacker to authenticate against arbitrary remote resources as another user.
CVE-2023-23397 describes a Critical Elevation of Privilege vulnerability affecting Outlook for Windows, which is concerning for several reasons. Microsoft has detected in-the-wild exploitation by a Russia-based threat actor targeting government, military, and critical infrastructure targets in Europe.
An attacker could use a specially-crafted email to cause Outlook to send NTLM authentication messages to an attacker-controlled SMB share, and can then use that information to authenticate against other services offering NTLM authentication. Given the network attack vector, the ubiquity of SMB shares, and the lack of user interaction required, an attacker with a suitable existing foothold on a network may well consider this vulnerability a prime candidate for lateral movement.
The vulnerability was discovered by Microsoft Threat Intelligence, who have published a Microsoft Security Research Center blog post describing the issue in detail, and which provides a Microsoft script and accompanying documentation to detect if an asset has been compromised using CVE-2023-23397.
Current self-hosted versions of Outlook – including Microsoft 365 Apps for Enterprise – are vulnerable to CVE-2023-23397, but Microsoft-hosted online services (e.g., Microsoft 365) are not vulnerable. Microsoft has calculated a CVSSv3 base score of 9.8.
The other zero-day vulnerability this month, CVE-2023-24880, describes a Security Feature Bypass in Windows SmartScreen, which is part of Microsoft’s slate of endpoint protection offerings. A specially crafted file could avoid receiving Mark of the Web and thus dodge the enhanced scrutiny usually applied to files downloaded from the internet.
Although Microsoft has seen in-the-wild exploitation, and original reporter Google TAG has linked CVE-2023-24880 to delivery of Magniber malware, Microsoft has assessed it as only Moderate severity – the only one this month – and assigned it a relatively low CVSSv3 base score of 5.4; the low impact ratings and requirement for user interaction contribute to the lower scoring. This vulnerability thus has the unusual distinction of being both an exploited-in-the-wild zero-day vulnerability and also the lowest-ranked vulnerability on Microsoft's severity scale in this month's Patch Tuesday. Only more recent versions of Windows are affected: Windows 10 and 11, as well as Server 2016 onwards.
A further five critical Remote Code Execution (RCE) vulnerabilities are patched this month in Windows low-level components. Three of these are assessed as Exploitation More Likely, and most of them affect a wide range of Windows versions, with the exception of CVE-2023-23392 which affects only Windows 11 and Windows Server 2022. Only assets where HTTP/3 has been enabled are potentially vulnerable – it is disabled by default – yet Microsoft still assesses this vulnerability as Exploitation More Likely, perhaps because HTTP endpoints are typically accessible.
CVE-2023-21708 is a Remote Procedure Call (RPC) vulnerability with a base CVSSv3 of 9.8. Microsoft recommends blocking TCP port 135 at the perimeter as a mitigation; given the perennial nature of RPC vulnerabilities, defenders will know that this has always been good advice.
Another veteran class of vulnerability makes a return this month: CVE-2023-23415 describes an attack involving a fragmented packet inside the header of another ICMP packet. Insufficient validation of ICMP packets has been a source of vulnerabilities since the dawn of time; the original and still-infamous Ping of Death vulnerability, which affected a wide range of vendors and operating systems, was one of the first vulnerabilities ever to be assigned a CVE, way back in 1999.
Rounding out the remaining Critical RCE vulnerabilities this month are a malicious certificate attack leading to Arbitrary Code Execution (ACE), and an attack against Windows Remote Access Server (RAS) which happily requires the attacker to win a race condition and is thus harder to exploit.
Microsoft has addressed two related vulnerabilities introduced via the Trusted Platform Module (TPM) 2.0 reference implementation code published by the Trusted Computing Group industry alliance. CVE-2023-1017 is an out-of-bounds write, and CVE-2023-1018 is an out-of-bounds read. Both may be triggered without elevated privileges, and may allow an attacker to access or modify highly-privileged information inside the TPM itself. Defenders managing non-Microsoft assets should note that a wide range of vendors including widely used Linux distros are also affected by this pair of vulnerabilities.
Admins who still remember the aptly-named PrintNightmare vulnerability from the summer of 2021 may well raise a wary eyebrow at this month’s batch of 18 fixes for the Microsoft PostScript and PCL6 Class Printer Driver, but there’s no sign that any of these are cause for the same level of concern, not least because there has been no known public disclosure prior to Microsoft releasing patches.
Azure administrators who update their Service Fabric Cluster manually should note that CVE-2023-23383 describes a spoofing vulnerability in the web management client where a user clicking a suitably-crafted malicious link could unwittingly execute actions against the remote cluster. Azure estates with automatic upgrades enabled are already protected.
Summary charts
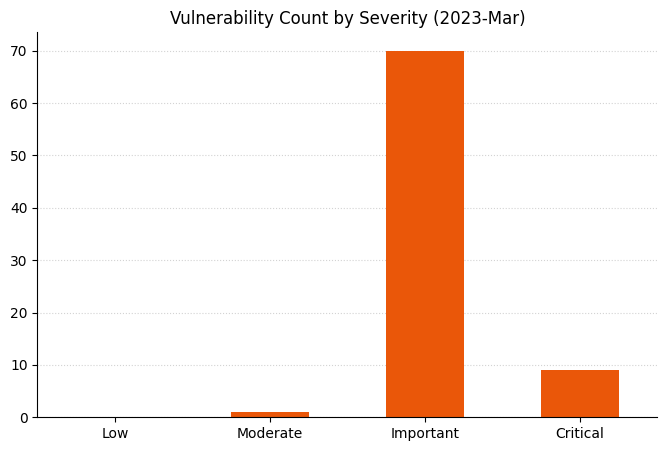
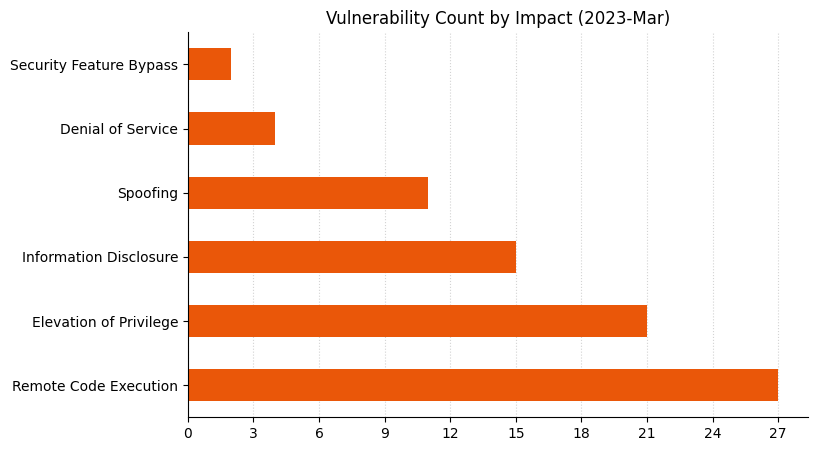
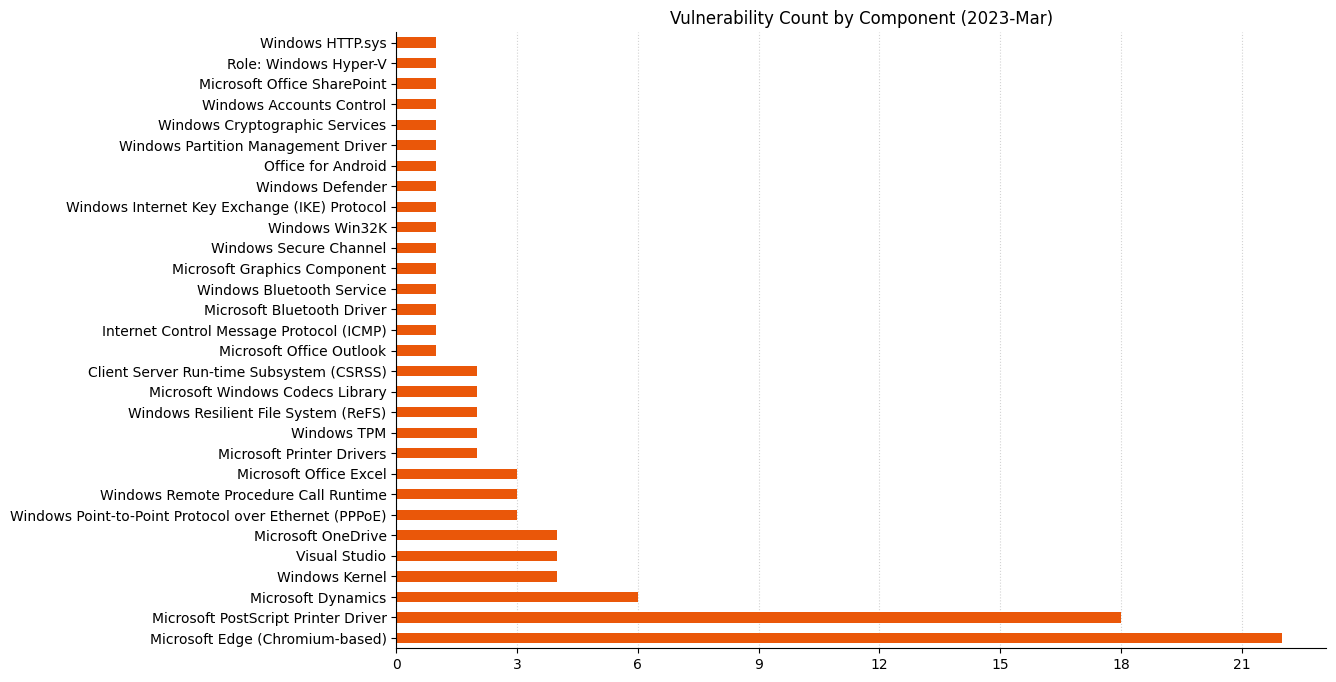
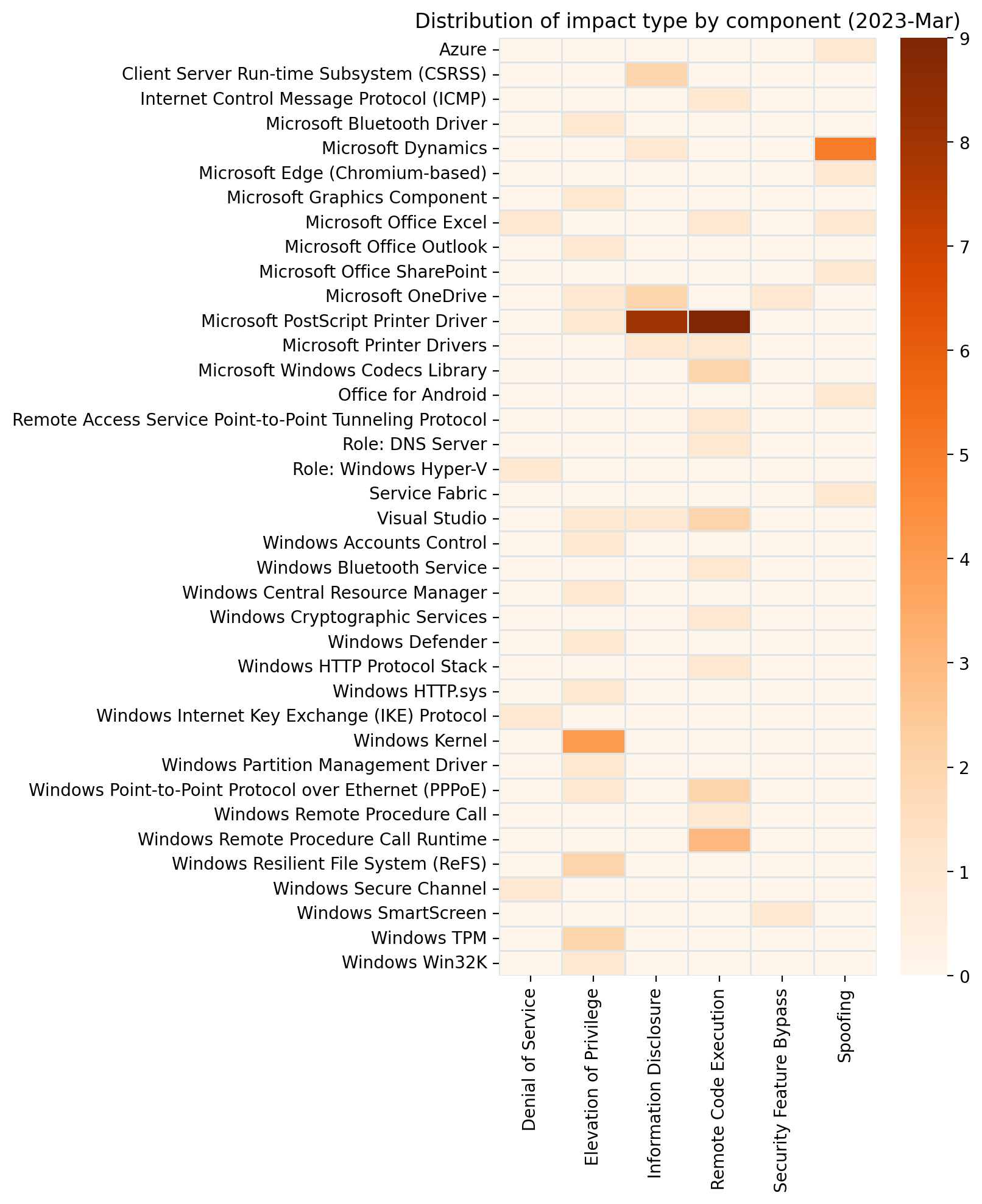
Summary tables
Apps vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24890 | Microsoft OneDrive for iOS Security Feature Bypass Vulnerability | No | No | 6.5 |
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23383 | Service Fabric Explorer Spoofing Vulnerability | No | No | 8.2 |
| CVE-2023-23408 | Azure Apache Ambari Spoofing Vulnerability | No | No | 4.5 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24892 | Microsoft Edge (Chromium-based) Webview2 Spoofing Vulnerability | No | No | 7.1 |
| CVE-2023-1236 | Chromium: CVE-2023-1236 Inappropriate implementation in Internals | No | No | N/A |
| CVE-2023-1235 | Chromium: CVE-2023-1235 Type Confusion in DevTools | No | No | N/A |
| CVE-2023-1234 | Chromium: CVE-2023-1234 Inappropriate implementation in Intents | No | No | N/A |
| CVE-2023-1233 | Chromium: CVE-2023-1233 Insufficient policy enforcement in Resource Timing | No | No | N/A |
| CVE-2023-1232 | Chromium: CVE-2023-1232 Insufficient policy enforcement in Resource Timing | No | No | N/A |
| CVE-2023-1231 | Chromium: CVE-2023-1231 Inappropriate implementation in Autofill | No | No | N/A |
| CVE-2023-1230 | Chromium: CVE-2023-1230 Inappropriate implementation in WebApp Installs | No | No | N/A |
| CVE-2023-1229 | Chromium: CVE-2023-1229 Inappropriate implementation in Permission prompts | No | No | N/A |
| CVE-2023-1228 | Chromium: CVE-2023-1228 Insufficient policy enforcement in Intents | No | No | N/A |
| CVE-2023-1224 | Chromium: CVE-2023-1224 Insufficient policy enforcement in Web Payments API | No | No | N/A |
| CVE-2023-1223 | Chromium: CVE-2023-1223 Insufficient policy enforcement in Autofill | No | No | N/A |
| CVE-2023-1222 | Chromium: CVE-2023-1222 Heap buffer overflow in Web Audio API | No | No | N/A |
| CVE-2023-1221 | Chromium: CVE-2023-1221 Insufficient policy enforcement in Extensions API | No | No | N/A |
| CVE-2023-1220 | Chromium: CVE-2023-1220 Heap buffer overflow in UMA | No | No | N/A |
| CVE-2023-1219 | Chromium: CVE-2023-1219 Heap buffer overflow in Metrics | No | No | N/A |
| CVE-2023-1218 | Chromium: CVE-2023-1218 Use after free in WebRTC | No | No | N/A |
| CVE-2023-1217 | Chromium: CVE-2023-1217 Stack buffer overflow in Crash reporting | No | No | N/A |
| CVE-2023-1216 | Chromium: CVE-2023-1216 Use after free in DevTools | No | No | N/A |
| CVE-2023-1215 | Chromium: CVE-2023-1215 Type Confusion in CSS | No | No | N/A |
| CVE-2023-1214 | Chromium: CVE-2023-1214 Type Confusion in V8 | No | No | N/A |
| CVE-2023-1213 | Chromium: CVE-2023-1213 Use after free in Swiftshader | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23946 | GitHub: CVE-2023-23946 mingit Remote Code Execution Vulnerability | No | No | N/A |
| CVE-2023-23618 | GitHub: CVE-2023-23618 Git for Windows Remote Code Execution Vulnerability | No | No | N/A |
| CVE-2023-22743 | GitHub: CVE-2023-22743 Git for Windows Installer Elevation of Privilege Vulnerability | No | No | N/A |
| CVE-2023-22490 | GitHub: CVE-2023-22490 mingit Information Disclosure Vulnerability | No | No | N/A |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-21708 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-23415 | Internet Control Message Protocol (ICMP) Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-23405 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-24908 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-24869 | Remote Procedure Call Runtime Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-23401 | Windows Media Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-23402 | Windows Media Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-23420 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23421 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23422 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23423 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23410 | Windows HTTP.sys Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23407 | Windows Point-to-Point Protocol over Ethernet (PPPoE) Remote Code Execution Vulnerability | No | No | 7.1 |
| CVE-2023-23414 | Windows Point-to-Point Protocol over Ethernet (PPPoE) Remote Code Execution Vulnerability | No | No | 7.1 |
| CVE-2023-23385 | Windows Point-to-Point Protocol over Ethernet (PPPoE) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-24861 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-24862 | Windows Secure Channel Denial of Service Vulnerability | No | No | 5.5 |
| CVE-2023-23394 | Client Server Run-Time Subsystem (CSRSS) Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-23409 | Client Server Run-Time Subsystem (CSRSS) Information Disclosure Vulnerability | No | No | 5.5 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24922 | Microsoft Dynamics 365 Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24919 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 |
| CVE-2023-24879 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 |
| CVE-2023-24920 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 |
| CVE-2023-24891 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 |
| CVE-2023-24921 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 4.1 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23397 | Microsoft Outlook Elevation of Privilege Vulnerability | Yes | No | 9.8 |
| CVE-2023-24930 | Microsoft OneDrive for MacOS Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23399 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2023-23398 | Microsoft Excel Spoofing Vulnerability | No | No | 7.1 |
| CVE-2023-23396 | Microsoft Excel Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-23391 | Office for Android Spoofing Vulnerability | No | No | 5.5 |
| CVE-2023-24923 | Microsoft OneDrive for Android Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-24882 | Microsoft OneDrive for Android Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2023-23395 | Microsoft SharePoint Server Spoofing Vulnerability | No | No | 3.1 |
Microsoft Office ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-24910 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 7.8 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23389 | Microsoft Defender Elevation of Privilege Vulnerability | No | No | 6.3 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2023-23392 | HTTP Protocol Stack Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2023-24871 | Windows Bluetooth Service Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-23388 | Windows Bluetooth Driver Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-23403 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-23406 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-23413 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24867 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24907 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24868 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24909 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24872 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24913 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24876 | Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2023-24864 | Microsoft PostScript and PCL6 Class Printer Driver Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-1018 | CERT/CC: CVE-2023-1018 TPM2.0 Module Library Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-1017 | CERT/CC: CVE-2023-1017 TPM2.0 Module Library Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2023-23416 | Windows Cryptographic Services Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2023-23404 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2023-23418 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23419 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23417 | Windows Partition Management Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-23412 | Windows Accounts Picture Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2023-24859 | Windows Internet Key Exchange (IKE) Extension Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2023-23400 | Windows DNS Server Remote Code Execution Vulnerability | No | No | 7.2 |
| CVE-2023-23393 | Windows BrokerInfrastructure Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2023-23411 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2023-24856 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24857 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24858 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24863 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24865 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24866 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24906 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24870 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24911 | Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2023-24880 | Windows SmartScreen Security Feature Bypass Vulnerability | Yes | Yes | 5.4 |
Note that Microsoft has not provided CVSSv3 scores for vulnerabilities in Chromium, which is an open-source software consumed by Microsoft Edge. Chrome, rather than Microsoft, is the assigning CNA for Chromium vulnerabilities. Microsoft documents this class of vulnerability in the Security Upgrade Guide to announce that the latest version of Microsoft Edge (Chromium-based) is no longer vulnerable.

