Microsoft is addressing 73 vulnerabilities this February 2024 Patch Tuesday, including two (actually, three!) zero-day/exploited-in-the-wild vulnerabilities, both of which are already included on the CISA KEV list. Today also brings patches for two critical remote code execution (RCE) vulnerabilities, and a critical elevation of privilege vulnerability in Exchange. Six browser vulnerabilities were published separately this month, and are not included in the total.
Windows SmartScreen: exploited-in-the-wild critical security bypass
CVE-2024-21351 describes a security feature bypass vulnerability in Windows SmartScreen. Microsoft has already seen evidence of exploitation in the wild. Successful exploitation requires that the attacker convince the user to open a malicious file. Successful exploitation bypasses the SmartScreen user experience and potentially allows code injection into SmartScreen to achieve remote code execution. Of interest: other critical SmartScreen bypass vulnerabilities from the past couple of years (e.g. CVE-2023-36025 from November 2023) have not included language describing code injection into SmartScreen itself, focusing instead on the security feature bypass only. Microsoft’s own researchers reported both CVE-2024-21351 and CVE-2023-36025.
Internet Shortcut files: exploited-in-the-wild security bypass
If further evidence were ever needed that clicking Internet Shortcut files from unknown sources is typically a bad idea, CVE-2024-21412 provides it. An attacker who convinces a user to open a malicious Internet Shortcut file can bypass the typical dialog which warns that “files from the internet can potentially harm your computer”. Microsoft notes that it has seen exploitation in the wild, although the requirement for user interaction helps keep the severity rating below critical, both for CVSS and Microsoft’s proprietary ranking system.
Microsoft Office: critical RCE
Microsoft Office typically shields users from a variety of attacks by opening files with Mark of the Web in Protected View, which means Office will render the document without fetching potentially malicious external resources. CVE-2024-21413 is a critical RCE vulnerability in Office which allows an attacker to cause a file to open in editing mode as though the user had agreed to trust the file. The Outlook Preview Pane is listed as an attack vector, and no user interaction is required. Microsoft assesses this vulnerability as a critical CVSSv3 base score of 9.8, as well as critical under their own proprietary severity ranking scale. Administrators responsible for Office 2016 installations who apply patches outside of Microsoft Update should note that the advisory lists no fewer than five separate patches which must be installed to achieve remediation of CVE-2024-21413; individual update KB articles further note that partially-patched Office installations will be blocked from starting until the correct combination of patches has been installed.
Windows PGM: critical RCE
Microsoft is patching CVE-2024-21357, a flaw in Windows Pragmatic General Multicast (PGM). When thus vulnerability was first published on Patch Tuesday, the CVSSv3 base score was a relatively mild 7.5, but a day later Microsoft adjusted the CVSSv3 base score so that the Attack Vector was switched from Adjacent to Network, which bumps the CVSSv3 base score up to 8.1. Exploitability language in the FAQ was adjusted from "limited to systems on the same network switch or virtual network" to "Windows Pragmatic General Multicast (PGM) produces multicast traffic that runs on layer 4 and is routable. Therefore this vulnerability can be exploited over the network". This adjustment — which the advisory rather optimistically describes as an informational change only — increases the potential risk posed by CVE-2024-21357.
Unsurprisingly, Microsoft rates CVE-2024-21357 as critical under its own proprietary severity scale. A discrepancy between the two severity ranking systems is always worth noting, and this has quickly proven to be the case here.
A further clue that Microsoft considers this vulnerability particularly serious: patches are available for Windows Server 2008, which is now completely end of life. The advisory is light on detail when it comes to exploitation methods; other recent critical RCE vulnerabilities in Windows PGM have involved Microsoft Message Queuing Service.
Exchange: critical elevation of privilege
Exchange admins may have enjoyed a rare two-month break from patching, but this month sees the publication of CVE-2024-21410, a critical elevation of privilege vulnerability in Exchange. Microsoft explains that an attacker could use NTLM credentials previously acquired via another means to act as the victim on the Exchange server using an NTLM relay attack. One possible avenue for that credential acquisition: an NTLM credential-leaking vulnerability in Outlook such as CVE-2023-36761, which Rapid7 wrote about back in September 2023.
Compounding the concern for defenders: Exchange 2016 is listed as affected, but no patch is yet listed on the CVE-2024-21410 advisory. Exchange 2019 patches are available for CU13 and the newly minted CU14 series. According to Microsoft, Exchange installations where Extended Protection for Authentication (EPA) is already enabled are protected, although Microsoft strongly recommends installing the latest Cumulative Update. Further resources are provided on the advisory, including Microsoft’s generic guidance on mitigating Pass the Hash-style attacks, as well as Microsoft’s Exchange Server Health Checker script, which includes an overview of EPA status. The Exchange 2019 CU14 update series enables EPA by default.
A day after initial publication, Microsoft updated the advisory for CVE-2024-21410 to indicate that they had in fact previously been aware of exploitation.
Lifecycle update
There are no significant end-of-lifecycle changes for Microsoft products this month.
Summary Charts
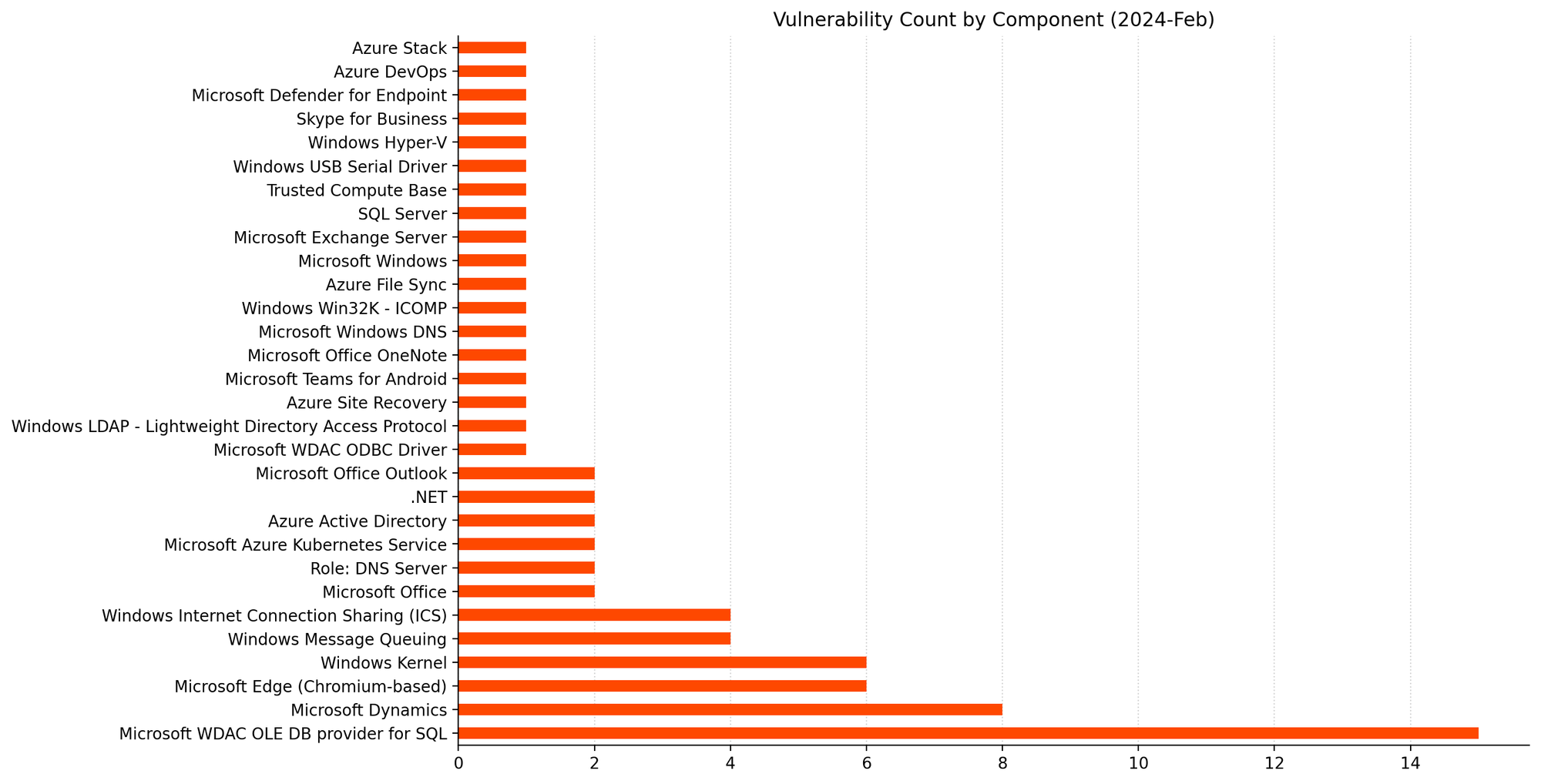
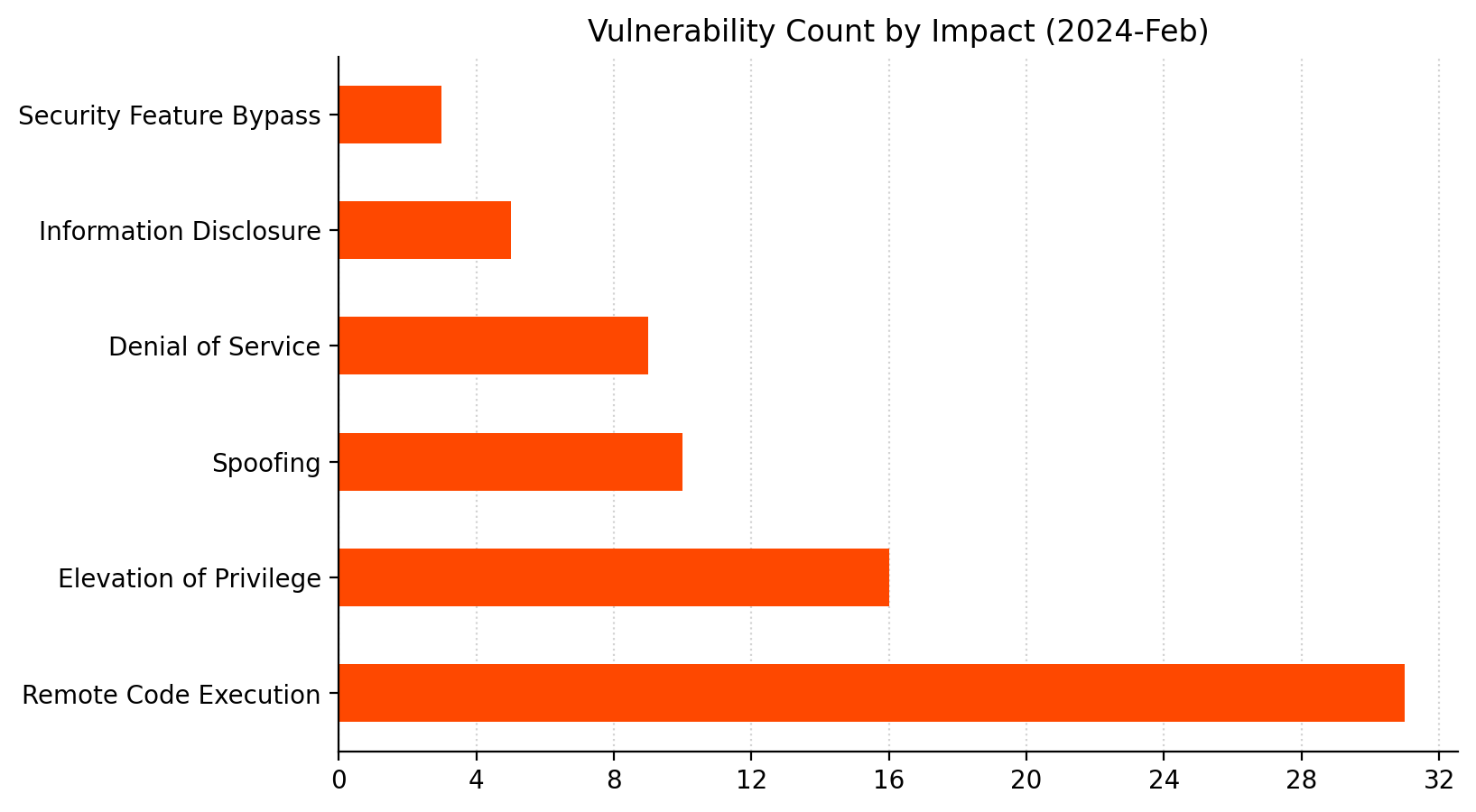
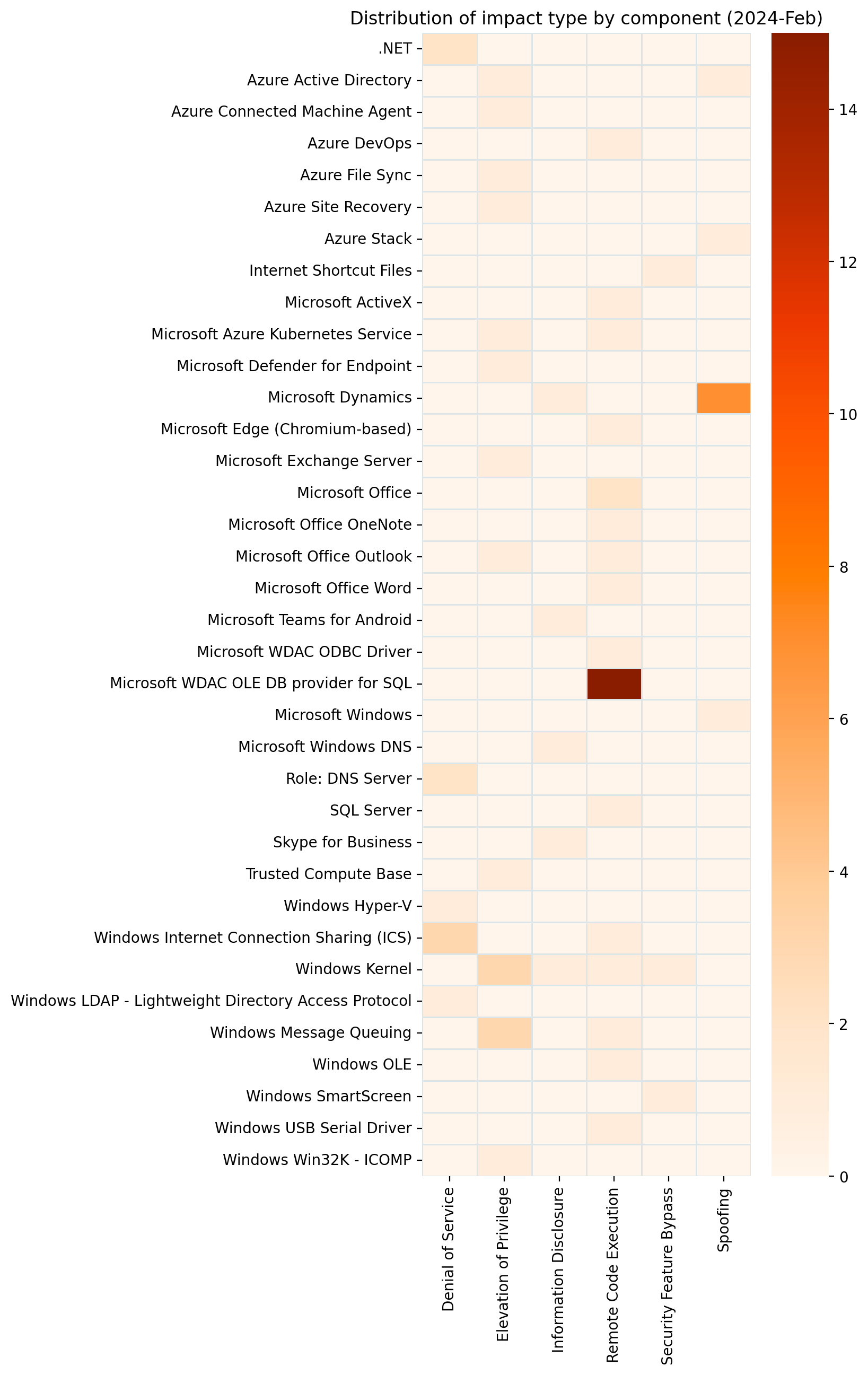
Summary Tables
Azure vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21401 | Microsoft Entra Jira Single-Sign-On Plugin Elevation of Privilege Vulnerability | No | No | 9.8 |
| CVE-2024-21364 | Microsoft Azure Site Recovery Elevation of Privilege Vulnerability | No | No | 9.3 |
| CVE-2024-21376 | Microsoft Azure Kubernetes Service Confidential Container Remote Code Execution Vulnerability | No | No | 9 |
| CVE-2024-21403 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability | No | No | 9 |
| CVE-2024-21329 | Azure Connected Machine Agent Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2024-21381 | Microsoft Azure Active Directory B2C Spoofing Vulnerability | No | No | 6.8 |
| CVE-2024-20679 | Azure Stack Hub Spoofing Vulnerability | No | No | 6.5 |
| CVE-2024-21397 | Microsoft Azure File Sync Elevation of Privilege Vulnerability | No | No | 5.3 |
Azure Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-20667 | Azure DevOps Server Remote Code Execution Vulnerability | No | No | 7.5 |
Browser vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21399 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | No | No | 8.3 |
| CVE-2024-1284 | Chromium: CVE-2024-1284 Use after free in Mojo | No | No | N/A |
| CVE-2024-1283 | Chromium: CVE-2024-1283 Heap buffer overflow in Skia | No | No | N/A |
| CVE-2024-1077 | Chromium: CVE-2024-1077 Use after free in Network | No | No | N/A |
| CVE-2024-1060 | Chromium: CVE-2024-1060 Use after free in Canvas | No | No | N/A |
| CVE-2024-1059 | Chromium: CVE-2024-1059 Use after free in WebRTC | No | No | N/A |
Developer Tools vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21386 | .NET Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-21404 | .NET Denial of Service Vulnerability | No | No | 7.5 |
ESU Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21372 | Windows OLE Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21350 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21352 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21358 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21360 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21361 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21366 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21369 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21375 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21420 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21359 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21365 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21367 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21368 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21370 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21391 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21349 | Microsoft ActiveX Data Objects Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21363 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-21354 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-21406 | Windows Printing Service Spoofing Vulnerability | No | No | 7.5 |
| CVE-2024-21357 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-21347 | Microsoft ODBC Driver Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2024-21348 | Internet Connection Sharing (ICS) Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-21377 | Windows DNS Information Disclosure Vulnerability | No | No | 7.1 |
| CVE-2024-21371 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-21355 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-21405 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2024-21356 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2024-21343 | Windows Network Address Translation (NAT) Denial of Service Vulnerability | No | No | 5.9 |
| CVE-2024-21344 | Windows Network Address Translation (NAT) Denial of Service Vulnerability | No | No | 5.9 |
| CVE-2024-21340 | Windows Kernel Information Disclosure Vulnerability | No | No | 4.6 |
| CVE-2023-50387 | MITRE: CVE-2023-50387 DNSSEC verification complexity can be exploited to exhaust CPU resources and stall DNS resolvers | No | No | N/A |
Exchange Server vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21410 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | No | 9.8 |
Microsoft Dynamics vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21395 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 8.2 |
| CVE-2024-21380 | Microsoft Dynamics Business Central/NAV Information Disclosure Vulnerability | No | No | 8 |
| CVE-2024-21327 | Microsoft Dynamics 365 Customer Engagement Cross-Site Scripting Vulnerability | No | No | 7.6 |
| CVE-2024-21389 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2024-21393 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 7.6 |
| CVE-2024-21396 | Dynamics 365 Sales Spoofing Vulnerability | No | No | 7.6 |
| CVE-2024-21328 | Dynamics 365 Sales Spoofing Vulnerability | No | No | 7.6 |
| CVE-2024-21394 | Dynamics 365 Field Service Spoofing Vulnerability | No | No | 7.6 |
Microsoft Office vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21413 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2024-21378 | Microsoft Outlook Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2024-21379 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-20673 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-21384 | Microsoft Office OneNote Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2024-21402 | Microsoft Outlook Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2024-20695 | Skype for Business Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2024-21374 | Microsoft Teams for Android Information Disclosure | No | No | 5 |
System Center vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21315 | Microsoft Defender for Endpoint Protection Elevation of Privilege Vulnerability | No | No | 7.8 |
Windows vulnerabilities
| CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2024-21345 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2024-21353 | Microsoft WDAC ODBC Driver Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2024-21412 | Internet Shortcut Files Security Feature Bypass Vulnerability | Yes | No | 8.1 |
| CVE-2024-21338 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-21346 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2024-21351 | Windows SmartScreen Security Feature Bypass Vulnerability | Yes | No | 7.6 |
| CVE-2024-21342 | Windows DNS Client Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2024-21341 | Windows Kernel Remote Code Execution Vulnerability | No | No | 6.8 |
| CVE-2024-20684 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2024-21339 | Windows USB Generic Parent Driver Remote Code Execution Vulnerability | No | No | 6.4 |
| CVE-2024-21362 | Windows Kernel Security Feature Bypass Vulnerability | No | No | 5.5 |
| CVE-2024-21304 | Trusted Compute Base Elevation of Privilege Vulnerability | No | No | 4.1 |
Updates
- 2024-02-14: Updated Exchange vulnerability CVE-2024-21410 after Microsoft adjusted the advisory to indicate that they were aware of in-the-wild exploitation.
- 2024-02-14: Updated Windows PGM vulnerability CVE-2024-21357 after Microsoft adjusted the advisory to indicate that this vulnerability is exploitable across different networks, when they had previously indicated that attacks would be limited to the same network switch or VLAN.
NEVER MISS AN EMERGING THREAT
Be the first to learn about the latest vulnerabilities and cybersecurity news.
Subscribe Now
