Automated security scanners can be stopped in their tracks by Multi-Factor Authentication (MFA). While this is great for security, it poses a challenge for scanning. Luckily, Rapid7's InsightAppSec makes it easy to handle Time-based One-Time Passwords (TOTP), a six-digit code that refreshes every 30 seconds.
This guide will walk you through the entire process of configuring an InsightAppSec scan to bypass TOTP MFA, using the challenge site authenticationtest.com as our example.
https://authenticationtest.com/totpChallenge
Step 1: Extract the TOTP secret key
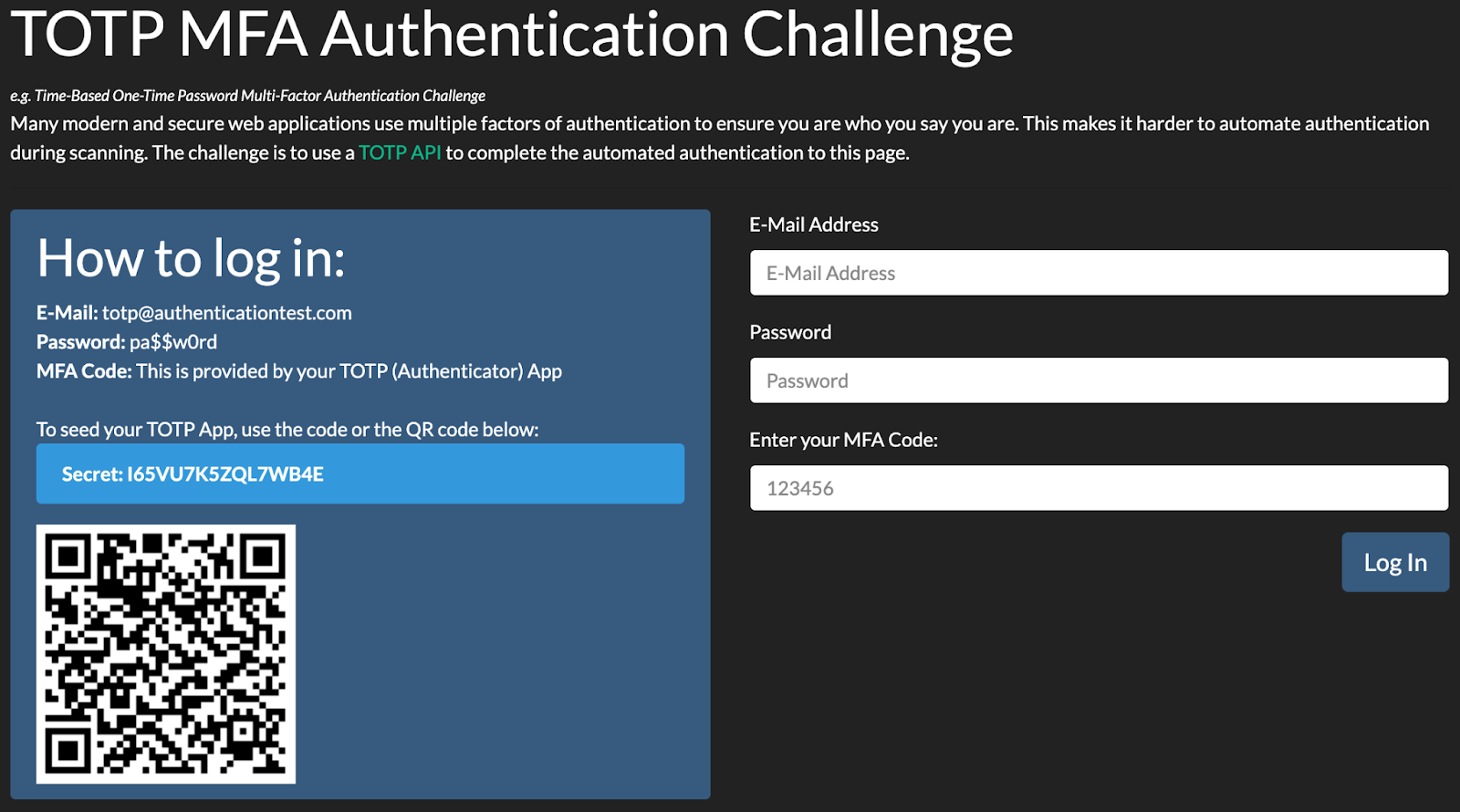
Before you can do anything else, you need the secret key that the application uses to generate its one-time passwords. This secret is embedded in the QR code.
You have two main options depending on how the QR code is encoded:
OTP Reader: If the QR code is not encoded, you can simply read it. Add the OTP to a password manager like 1Password, use a QR reader app like QR Journal on MacOS, or an online reader such as token2.com's TOTP Decoder.
OTP Decoder: If the QR code is encoded, such as ones exported from apps like Google Authenticator, you will need to decode it first. One way to do this is using extract_otp_secrets on Github.
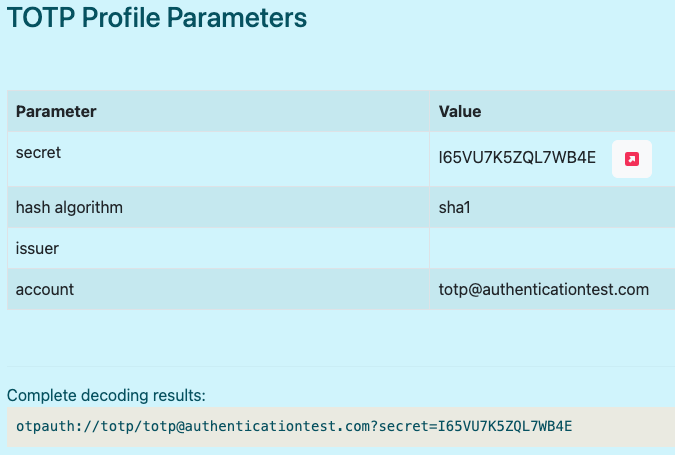
As you can see in the screenshot below, our simple QR code decodes to the following value: otpauth://totp/[email protected]?secret=I65VU7K5ZQL7WB4E
The most important part here is the secret parameter. You'll also want to note the hashing algorithm. If the algorithm isn't specified in the URI, the default is SHA1.
From there, we can put that secret into our app, and use it to login.
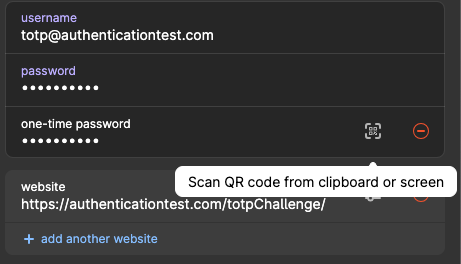
https://support.1password.com/one-time-passwords
Step 2: Record the login macro
Now, you need to record the login sequence so InsightAppSec can replay it.
Install the Rapid7 AppSec Plugin for Chrome.
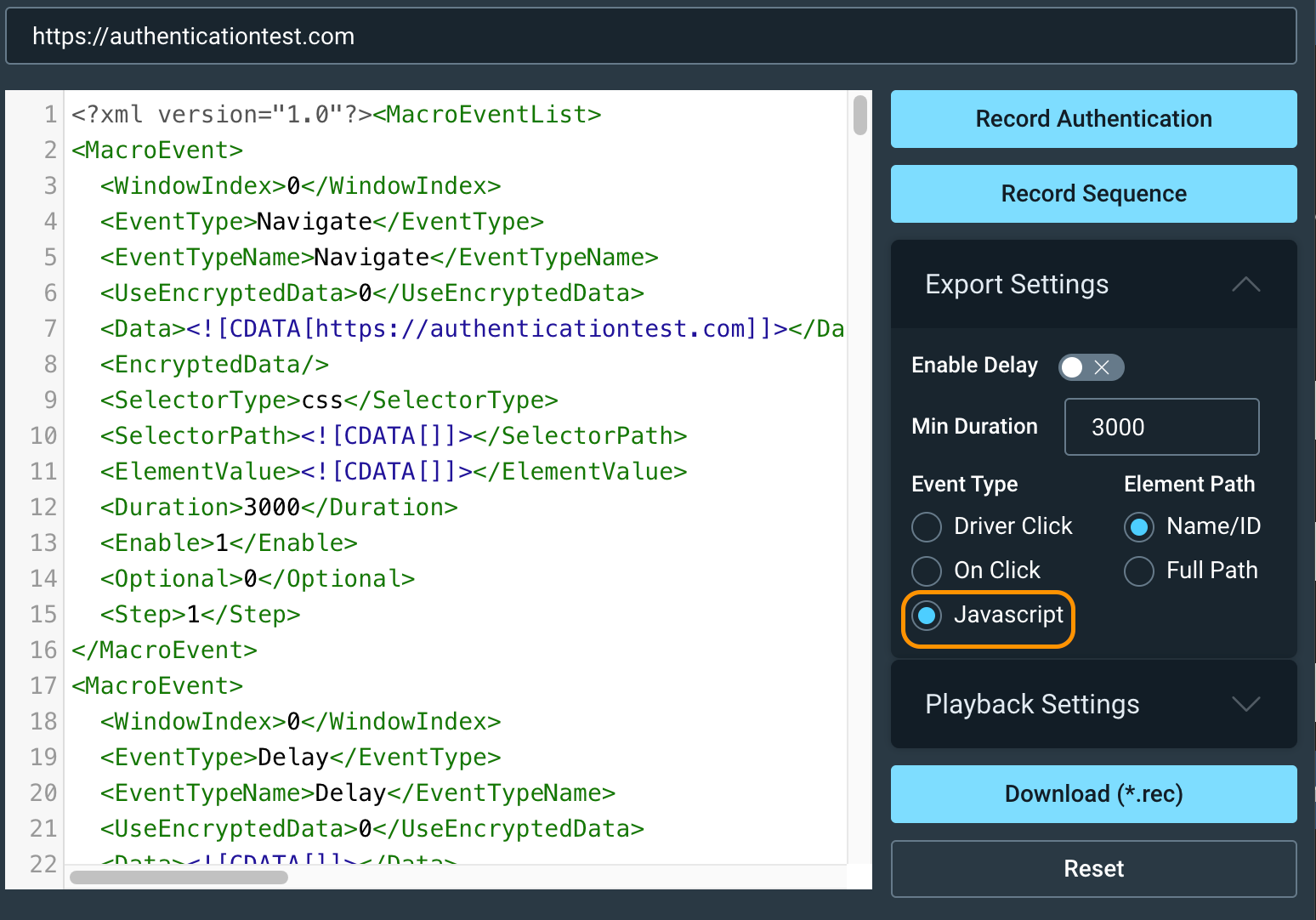
Open the plugin, input the app URL under “Macro Recorder” and click Record Authentication.
Perform the login on your target site (authenticationtest.com). Enter the username, password, and a currently valid OTP code from your authenticator app. Once logged in, stop the recording.
Important: In the export settings, change the Event Type to Javascript. This is crucial because InsightAppSec will use JavaScript to handle OTP form submissions.
Once complete, download the .rec file.
Step 3: Edit the macro for dynamic codes
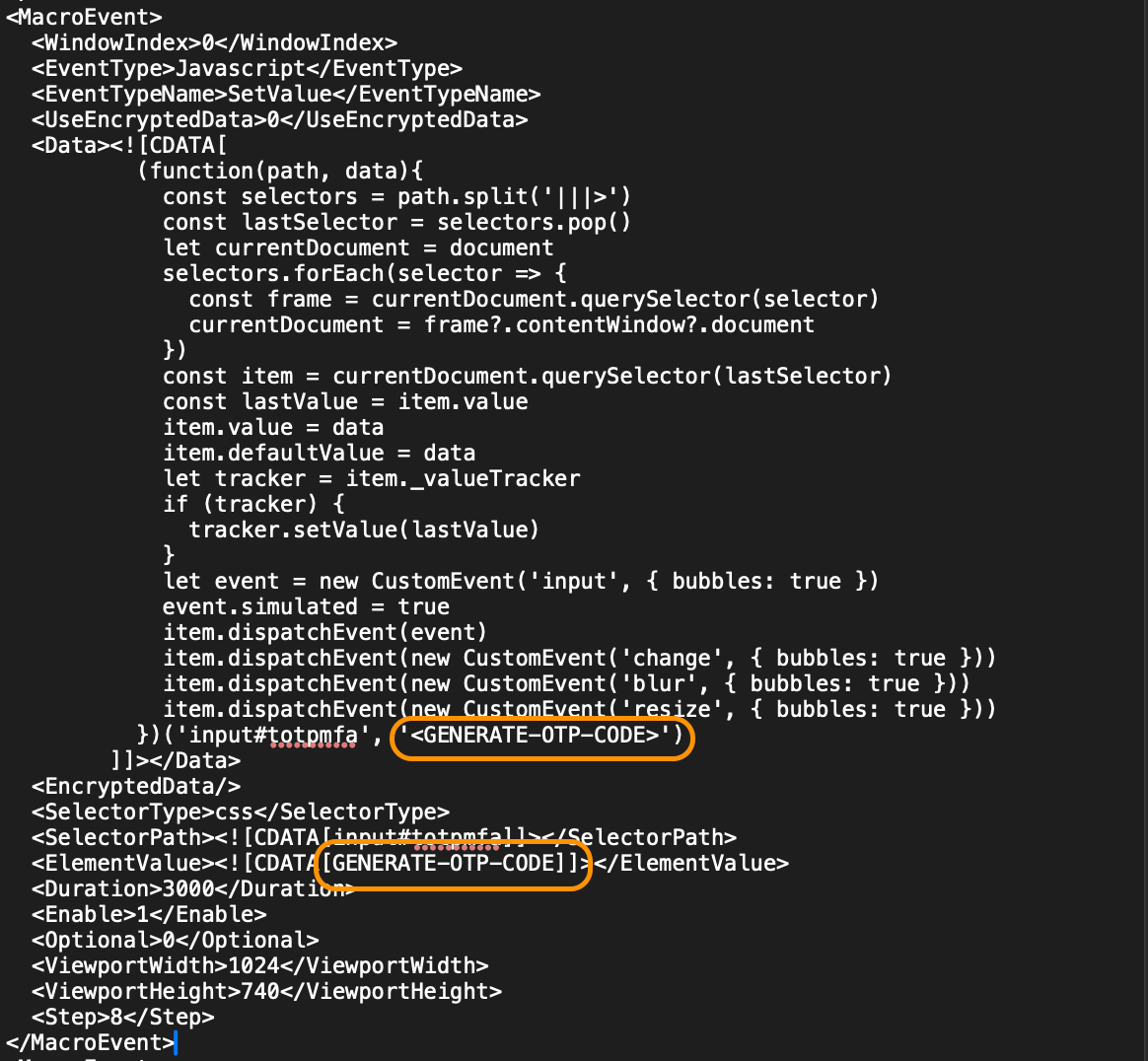
The macro file you just downloaded contains your recorded actions, including the specific OTP code you used. We need to replace that static code with a dynamic placeholder.
Open the downloaded .rec file in a text editor like TextEdit, Notepad++, or Vim. It's a simple XML file.
Search for the OTP code you entered during the recording (e.g., "345678").
Replace that static code with the special placeholder: GENERATE-OTP-CODE.
When InsightAppSec runs this macro, it will see this placeholder and automatically substitute it with a freshly generated, valid OTP code using the secret key you provide in the next step.
Step 4: Configure the InsightAppSec scan
Now it's time to put it all together in your InsightAppSec scan configuration.
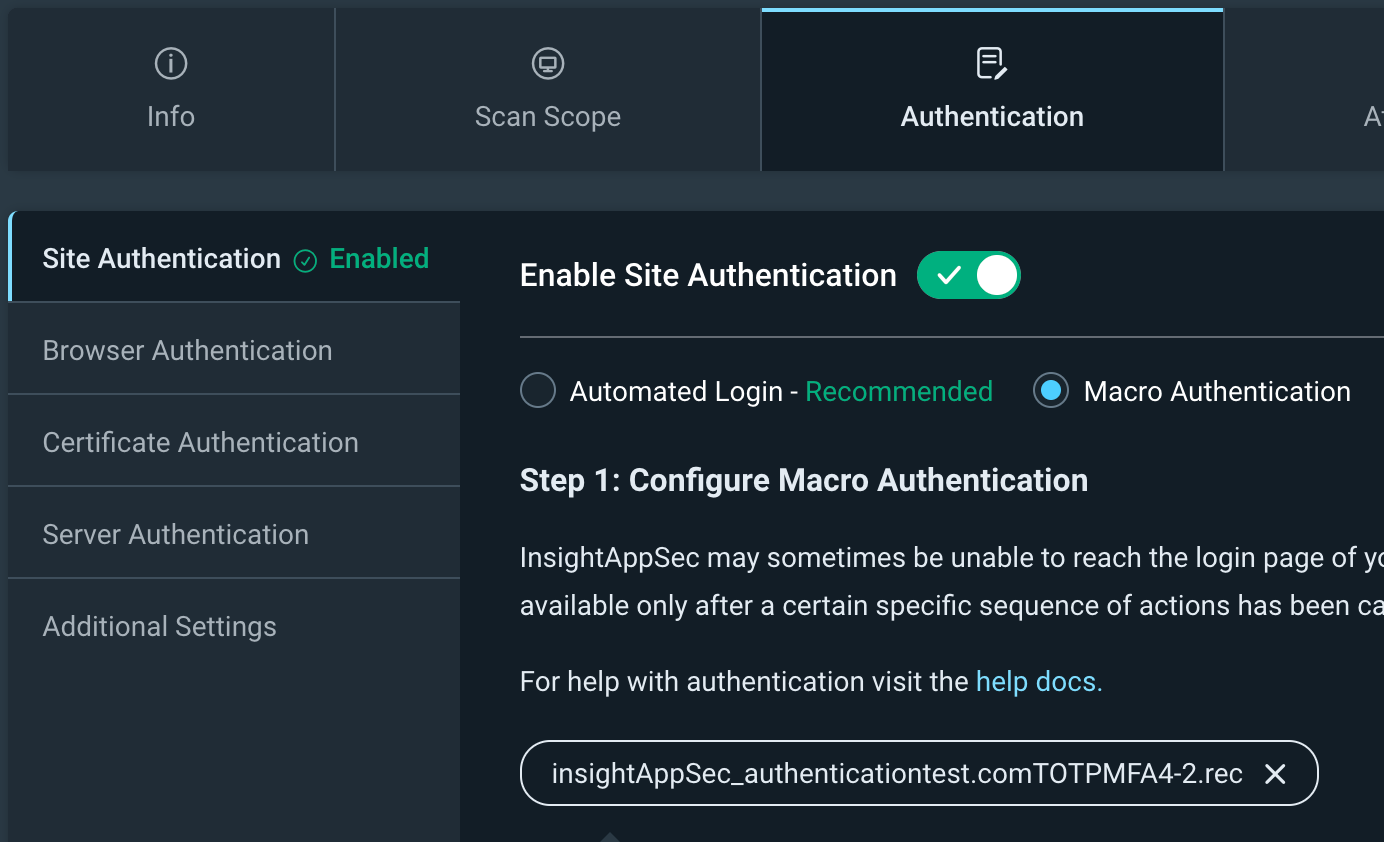
Navigate to your Scan Config and go to the Authentication tab.
Choose Macro as the authentication type and upload your edited .rec file.
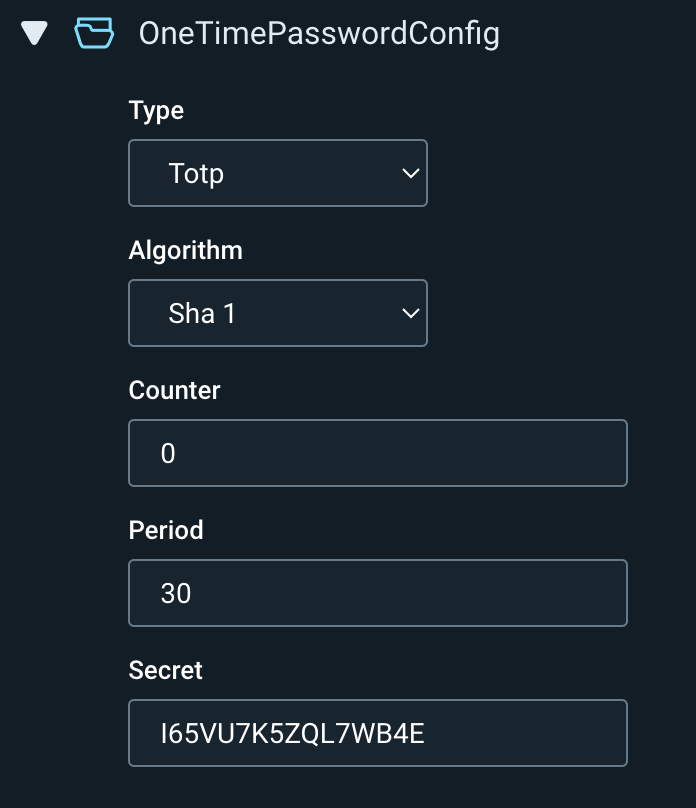
Navigate to Custom Options -> Advanced Options -> Auth Config -> OneTimePasswordConfig to add the MFA information.
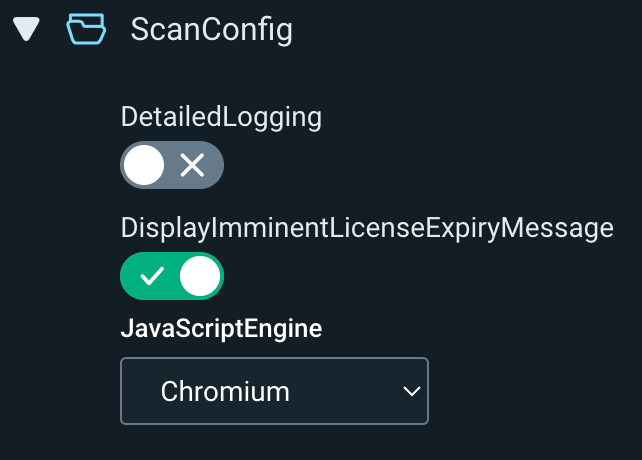
Finally, go to Custom Options -> Advanced Options -> ScanConfig -> JavaScriptEngine. Ensure the JavaScript Engine is set to Chromium. This modern engine is required to replace the dynamic placeholder in the macro. Another benefit of using Chromium is that it records a video of the authentication attempt, which is invaluable for troubleshooting.
Setting | Value | Explanation |
Type | TOTP | TOTP (for Time-based OTP), or HOTP (for HMAC-based OTP) |
Algorithm | SHA1 | Used to decode the secret |
Counter | 0 | HTOP only: Used along with the secret to generate a code, e.g. 0 |
Period | 30 | TOTP only: How long the key is valid for in seconds, e.g. 30 |
Secret | <Your Secret> | The OTP secret key (Will be redacted in the logs) |
Step 5: Launch and verify your scan
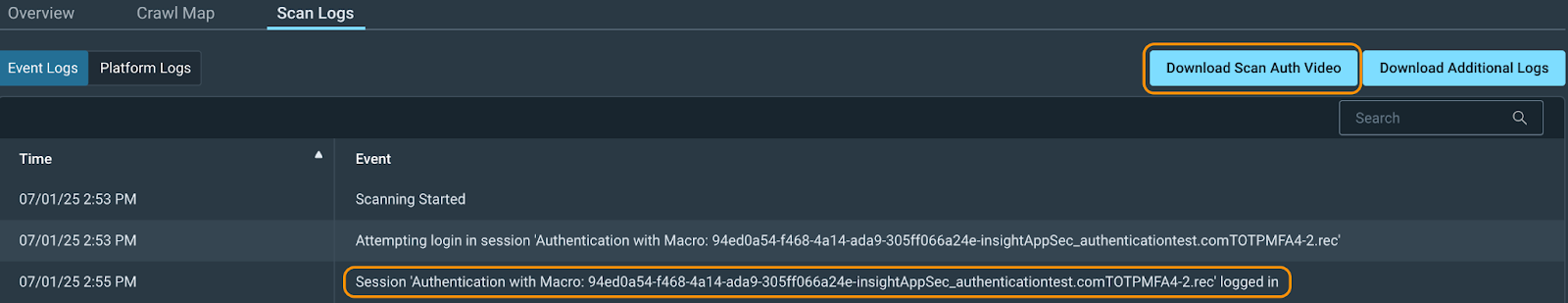
You're all set! Save your scan configuration and kick off the scan. You can check on the scan logs to see if it logged in successfully. From the scan logs, you can also download the Scan Auth Video once the scan is completeto ensure everything worked as it should.