Microsoft is addressing 111 vulnerabilities this August 2025 Patch Tuesday, a volume which is around the recent average. In a neat parallel with last month, Microsoft is aware of public disclosure for a single one of the vulnerabilities published today, and claims no evidence of in-the-wild exploitation. Once again, the lone Patch Tuesday zero-day vulnerability is assessed as only moderate severity at time of publication, which brings Microsoft’s lucky streak up to 11 months. Today’s release includes the publication of nine critical remote code execution (RCE) vulnerabilities, although Microsoft has only marked one of these as more likely to see exploitation. Eight browser vulnerabilities have already been published separately this month, and are not included in the total.
Kerberos: zero-day EoP
What do attackers want in a Windows context? Domain admin! When do they want it? Now! Today’s lone zero-day vulnerability might be just what they need to break through the final layers of protection and swipe the crown jewels. CVE-2025-53779 is an elevation of privilege (EoP) vulnerability in the Windows implementation of Kerberos, which is enabled via abuse of dMSA configuration. The advisory FAQ provides more clues as to the nature of the attack than many comparable Microsoft advisories, but misses a golden opportunity for clarity, since it never sets out what it means by dMSA, leaving us scouring for contextual clues. Ultimately, we can determine from context that today’s hot topic is the Delegated Managed Service Account, rather than the Defender Microservices Architecture or some other piece of Microsoft paraphernalia with matching initials. Microsoft’s motivation is unimpeachable: the dMSA supports automated rotation of credentials for service accounts, and is specifically designed to prevent credential harvesting using Kerberoasting. Indeed, CISA has described Kerberoasting as one of the most time-efficient ways to elevate privileges and move laterally throughout an organization’s network.
The good news here is that successful exploitation of CVE-2025-53779 requires an attacker to have pre-existing control of two attributes of the hopefully well protected dMSA: msds-groupMSAMembership, which determines which users may use credentials for the managed service account, and msds-ManagedAccountPrecededByLink, which contains a list of users on whose behalf the dMSA can act. However, abuse of CVE-2025-53779 is certainly plausible as the final link of a multi-exploit chain which stretches from no access to total pwnage. Finally, it’s important to note that Microsoft is only publishing patches for Windows Server 2025, and that’s because msds-ManagedAccountPrecededByLink was first implemented in Server 2025. Migrating to newer operating systems sooner rather than later remains good advice, but so is remediation of zero-day vulnerabilities which could give an attacker total control of your estate.
Windows Graphics: critical RCE
The publication of any pre-authentication RCE in Windows will naturally spark discussion. Of course, not all pre-auth RCEs are created equal, and while CVE-2025-50165 has a hefty CVSSv3 base score of 9.8, and is certainly a cause for concern, it is not the worst of the worst, since it presumably isn’t wormable. Despite that, a degree of alarm is amply justified, since the advisory FAQ mentions — twice! — that user interaction isn’t required. Exploitation is via a malicious JPEG file, which could be delivered within an Office document or other means; perhaps even visiting a website would be sufficient, or receiving an email within Outlook, although the advisory doesn’t explicitly confirm or deny these other possible attack routes. The malformed JPEG tricks the Windows Graphics Component into code execution via an untrusted pointer dereference. The context of execution isn’t specified, so in the standard spirit of caution, we’ll assume SYSTEM. This is hardly a new class of problem: we can cast our minds back a dozen years, for instance, and consider the broadly similar MS13-096. However, the specific flaw underlying CVE-2025-50165 is presumably a recent introduction, since only Windows 11 24H2 and Server 2025 receive patches. Patch this one sooner rather than later, since it could provide a skilled attacker with a valuable foothold from which to launch further attacks, including perhaps even today’s CVE-2025-53779.
Windows GDI+: critical RCE
The Windows GDI+ (Graphics Device Interface Plus) is at the center of how almost all two-dimensional graphics are rendered on Windows assets. CVE-2025-53766 is a critical RCE in how GDI+ interprets metafiles, which are often used to store vector graphics. An attacker can achieve code execution via buffer overflow without privileges or user interaction. As with today’s CVE-2025-50165, it’s unlikely that this vulnerability could be wormable, but the most alarming path to exploitation involved simply uploading a malicious metafile to a Windows machine running unspecified web services. There is no mention of SharePoint, Exchange, Office, or other non-Windows products in the Security Updates section of the advisory, but that still leaves an essentially limitless potential attack surface; for example, anyone running a custom ASP.NET application offering file uploads could find themselves vulnerable to an attacker wielding a dodgy WMF file. On the bright side, the Preview Pane is not a vector in this case. A patch is available for Server 2008, but not Server 2012, a curious and possibly concerning pattern that we see from time to time with RCEs which affect the full historic range of Windows products.
DirectX graphics kernel: critical RCE
Today is certainly a good day for fans of critical RCE vulnerabilities which target weaknesses in how Windows interprets graphics. Exploitation of CVE-2025-50176, a flaw in the DirectX graphics kernel, could lead to execution in a kernel context. Microsoft considers exploitation more likely, which may be why the advisory doesn’t provide a great deal of information about the means of exploitation, beyond a terse statement that type confusion is involved. Type confusion is where the kernel receives a pointer which it expects to be for one type of object, but is in fact for another, which is a bit like asking someone to read out loud from a restaurant menu, but then handing them their secret diary and hoping they won’t notice the difference. Most people will not be fooled, but under the right circumstances, anything is possible.
Microsoft lifecycle update
There are no significant changes to Microsoft product lifecycles this month. However, October will bring a flurry of changes, including the categorical end of support for non-LTSC versions of Windows 10.
Summary charts
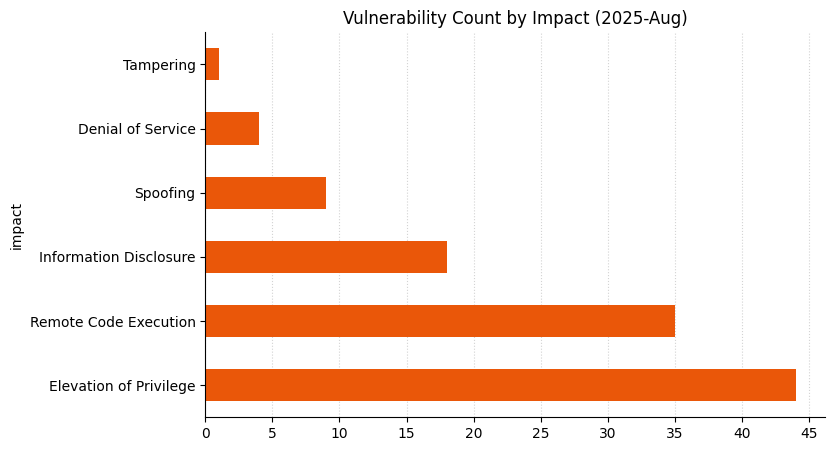
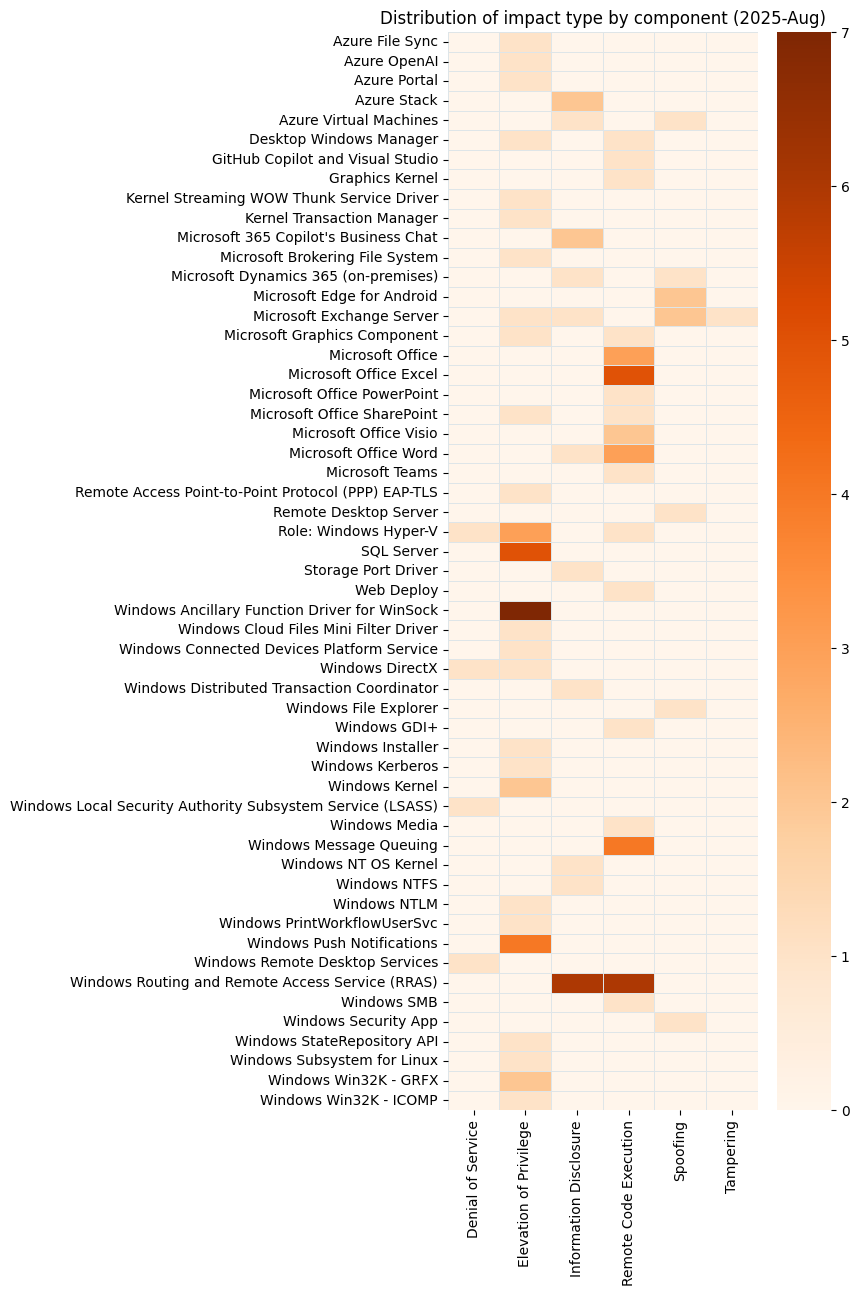
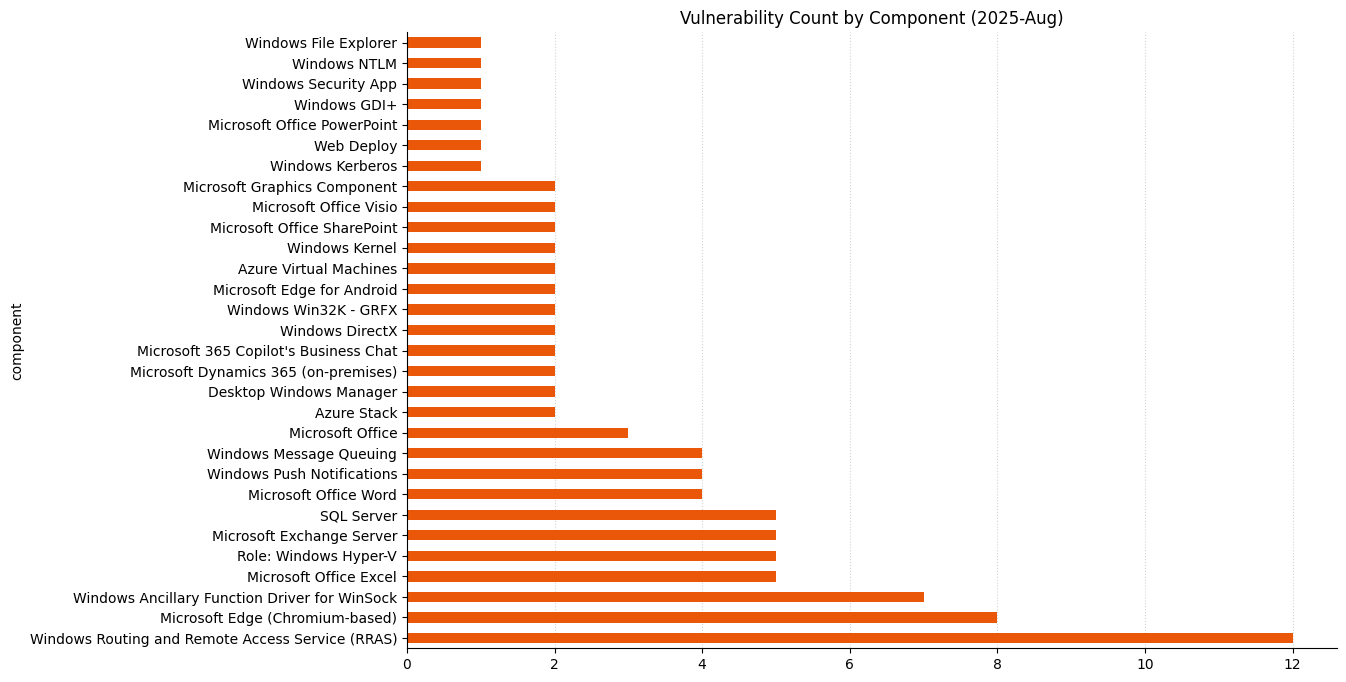
Summary tables
Apps vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53787 | Microsoft 365 Copilot BizChat Information Disclosure Vulnerability | No | No | 8.2 |
| CVE-2025-53774 | Microsoft 365 Copilot BizChat Information Disclosure Vulnerability | No | No | 6.5 |
Azure vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53767 | Azure OpenAI Elevation of Privilege Vulnerability | No | No | 10 |
| CVE-2025-53792 | Azure Portal Elevation of Privilege Vulnerability | No | No | 9.1 |
| CVE-2025-49707 | Azure Virtual Machines Spoofing Vulnerability | No | No | 7.9 |
| CVE-2025-53729 | Microsoft Azure File Sync Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53781 | Azure Virtual Machines Information Disclosure Vulnerability | No | No | 7.7 |
| CVE-2025-53793 | Azure Stack Hub Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2025-53765 | Azure Stack Hub Information Disclosure Vulnerability | No | No | 4.4 |
Browser vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-49736 | Microsoft Edge (Chromium-based) for Android Spoofing Vulnerability | No | No | 4.3 |
| CVE-2025-49755 | Microsoft Edge (Chromium-based) for Android Spoofing Vulnerability | No | No | 4.3 |
| CVE-2025-8583 | Chromium: CVE-2025-8583 Inappropriate implementation in Permissions | No | No | N/A |
| CVE-2025-8582 | Chromium: CVE-2025-8582 Insufficient validation of untrusted input in DOM | No | No | N/A |
| CVE-2025-8581 | Chromium: CVE-2025-8581 Inappropriate implementation in Extensions | No | No | N/A |
| CVE-2025-8580 | Chromium: CVE-2025-8580 Inappropriate implementation in Filesystems | No | No | N/A |
| CVE-2025-8579 | Chromium: CVE-2025-8579 Inappropriate implementation in Gemini Live in Chrome | No | No | N/A |
| CVE-2025-8578 | Chromium: CVE-2025-8578 Use after free in Cast | No | No | N/A |
| CVE-2025-8577 | Chromium: CVE-2025-8577 Inappropriate implementation in Picture In Picture | No | No | N/A |
| CVE-2025-8576 | Chromium: CVE-2025-8576 Use after free in Extensions | No | No | N/A |
Developer Tools vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53772 | Web Deploy Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53773 | GitHub Copilot and Visual Studio Remote Code Execution Vulnerability | No | No | 7.8 |
Device Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53783 | Microsoft Teams Remote Code Execution Vulnerability | No | No | 7.5 |
ESU Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-49757 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-50163 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53778 | Windows NTLM Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-53143 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53144 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53145 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-50177 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | No | No | 8.1 |
| CVE-2025-50160 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2025-50162 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2025-50164 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2025-53720 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | No | 8 |
| CVE-2025-53132 | Win32k Elevation of Privilege Vulnerability | No | No | 8 |
| CVE-2025-53724 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53725 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53726 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-50155 | Windows Push Notifications Apps Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-49761 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-50173 | Windows Installer Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53155 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53723 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53154 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53149 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53152 | Desktop Windows Manager Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-50153 | Desktop Windows Manager Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53722 | Windows Remote Desktop Services Denial of Service Vulnerability | No | No | 7.5 |
| CVE-2025-50154 | Microsoft Windows File Explorer Spoofing Vulnerability | No | No | 7.5 |
| CVE-2025-50161 | Win32k Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2025-50159 | Remote Access Point-to-Point Protocol (PPP) EAP-TLS Elevation of Privilege Vulnerability | No | No | 7.3 |
| CVE-2025-50158 | Windows NTFS Information Disclosure Vulnerability | No | No | 7 |
| CVE-2025-53140 | Windows Kernel Transaction Manager Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-50167 | Windows Hyper-V Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-49762 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53134 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53137 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53147 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53718 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53135 | DirectX Graphics Kernel Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-49743 | Windows Graphics Component Elevation of Privilege Vulnerability | No | No | 6.7 |
| CVE-2025-50166 | Windows Distributed Transaction Coordinator (MSDTC) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-50156 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-53138 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-53148 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-53153 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-53719 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-50157 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | No | 5.7 |
| CVE-2025-53136 | NT OS Kernel Information Disclosure Vulnerability | No | No | 5.5 |
ESU Windows Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53766 | GDI+ Remote Code Execution Vulnerability | No | No | 9.8 |
Microsoft Dynamics vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53728 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability | No | No | 6.5 |
| CVE-2025-49745 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | No | No | 5.4 |
Microsoft Office vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-49712 | Microsoft SharePoint Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53733 | Microsoft Word Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-53784 | Microsoft Word Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-53731 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-53740 | Microsoft Office Remote Code Execution Vulnerability | No | No | 8.4 |
| CVE-2025-53738 | Microsoft Word Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53761 | Microsoft PowerPoint Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53730 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53734 | Microsoft Office Visio Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53732 | Microsoft Office Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53741 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53759 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53735 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53737 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53739 | Microsoft Excel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-53760 | Microsoft SharePoint Elevation of Privilege Vulnerability | No | No | 7.1 |
| CVE-2025-53736 | Microsoft Word Information Disclosure Vulnerability | No | No | 6.8 |
Open Source Software vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53788 | Windows Subsystem for Linux (WSL2) Kernel Elevation of Privilege Vulnerability | No | No | 7 |
SQL Server vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-49758 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-53727 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-24999 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-49759 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
| CVE-2025-47954 | Microsoft SQL Server Elevation of Privilege Vulnerability | No | No | 8.8 |
Server Software vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-53786 | Microsoft Exchange Server Hybrid Deployment Elevation of Privilege Vulnerability | No | No | 8 |
| CVE-2025-33051 | Microsoft Exchange Server Information Disclosure Vulnerability | No | No | 7.5 |
| CVE-2025-25005 | Microsoft Exchange Server Tampering Vulnerability | No | No | 6.5 |
| CVE-2025-25006 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 5.3 |
| CVE-2025-25007 | Microsoft Exchange Server Spoofing Vulnerability | No | No | 5.3 |
Windows vulnerabilities
CVE | Title | Exploited? | Publicly disclosed? | CVSSv3 base score |
|---|---|---|---|---|
| CVE-2025-50165 | Windows Graphics Component Remote Code Execution Vulnerability | No | No | 9.8 |
| CVE-2025-50171 | Remote Desktop Spoofing Vulnerability | No | No | 9.1 |
| CVE-2025-53131 | Windows Media Remote Code Execution Vulnerability | No | No | 8.8 |
| CVE-2025-53789 | Windows StateRepository API Server file Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53133 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-53151 | Windows Kernel Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-50170 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-50168 | Win32k Elevation of Privilege Vulnerability | No | No | 7.8 |
| CVE-2025-50176 | DirectX Graphics Kernel Remote Code Execution Vulnerability | No | No | 7.8 |
| CVE-2025-50169 | Windows SMB Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2025-48807 | Windows Hyper-V Remote Code Execution Vulnerability | No | No | 7.5 |
| CVE-2025-53779 | Windows Kerberos Elevation of Privilege Vulnerability | No | Yes | 7.2 |
| CVE-2025-53721 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-53142 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | No | 7 |
| CVE-2025-49751 | Windows Hyper-V Denial of Service Vulnerability | No | No | 6.8 |
| CVE-2025-53716 | Local Security Authority Subsystem Service (LSASS) Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2025-50172 | DirectX Graphics Kernel Denial of Service Vulnerability | No | No | 6.5 |
| CVE-2025-53156 | Windows Storage Port Driver Information Disclosure Vulnerability | No | No | 5.5 |
| CVE-2025-53769 | Windows Security App Spoofing Vulnerability | No | No | 5.5 |

